Policy as code (PaC) is referred to as a policy management approach with the help of code to develop, amend, communicate, and enforce policies. Policy-as-code allows teams to move more quickly and reduces the possibility of human error by employing code-based automation rather than depending on manual processes to manage policies.
A Policy as code (PaC) approach to domains such as security enables policy definition and management in ways that different types of stakeholders - such as developers and security professionals EDR - can understand. This post discusses how Policy as code (PaC) works, why it's important, and how to use Policy as code (PaC) as a security factor.
Defining Policy as code (PaC)
To understand what Policy as code (PaC) entails, you must first define the term "policy." Any rule, condition, or instruction that governs IT operations or processes is referred to as a policy. A policy could be a rule that specifies which circumstances must be met for a code to pass a security check and be deployed. It could also be a series of operations that are automatically conducted in response to a security incident.
The use of code to design and manage rules and conditions is known as Policy as code (PaC). The specific terminology is usually determined by the Policy as code (PaC) management and enforcement tools being used.
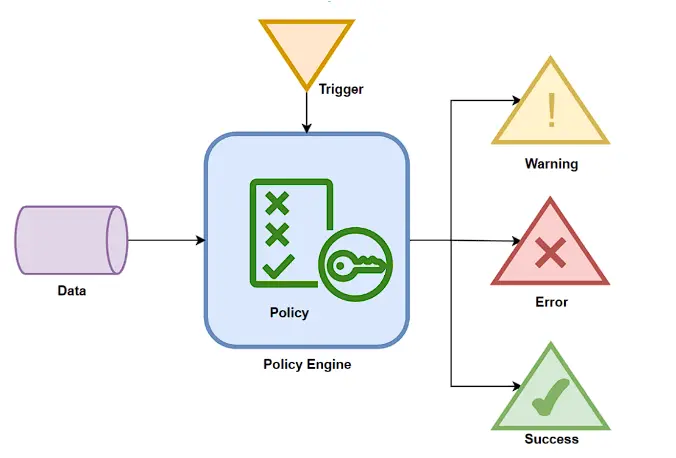
When engineers need to make changes, they edit and modify the existing code. They can also use version control systems (VCS) to share the code with others, giving them visibility into their policies. Finally, they can employ a Policy as code (PaC) enforcement engine to ensure that policies are followed.
Benefits of using Policy as code (PaC)
Over manual policy checks, the Policy as code (PaC) offers various advantages:
1. Quicker and more effective deployments
Policy as code (PaC) enables large-scale policy sharing and enforcement, which is far more efficient than manually applying policies. The capacity to automate results in more efficient processes. Engineers can detect mistakes or instances of noncompliance early in the software development cycle, resulting in better product delivery.
2. Automated testing, governance, and approvals
CI/CD solutions make it simple to automate policy testing, allowing you to uncover vulnerabilities and policy breaches and ensure policies are met before deployment. Policies can be defined using a graphical interface and then tested using a pull request workflow to ensure they maintain system behavior before merging.
3. Better at reliable and secure applications
Relying on engineers to manually evaluate hundreds of applications results in errors due to human error and conflicting interpretations of policies. Policy as code (PaC) enables policy enforcement to be consistent across the development lifecycle. The capability to organize policies into sets aids in policy management and enforcement.
4. Sandboxing
Policy as code (PaC) serves as a checkpoint for sandboxes, which are used to isolate programs from one another in order to prevent risky behavior. Because of the level of automation around sandboxes, manual verification is unfeasible; therefore, the Policy as code (PaC) is important for securely implementing sandboxes.
5. Collaboration
Having a systematic approach to writing and managing policies promotes collaboration both inside and between teams. For example, developers and security teams might collaborate to ensure that a release meets expectations. Also, the Policy as code (PaC) doesn't need developers to work with policymakers in order to obtain approval for every new release every time.
6. Infrastructure provisioning
Policy as code (PaC) can be used to create and implement infrastructure authorization and utilization policies, such as policies targeted at optimizing infrastructure utilization and enforcing firewalls. This means that businesses can benefit from cloud or hybrid infrastructure while also enhancing their security and compliance posture.
7. Better version control
The benefits of version control management are brought to policy administration by storing policies as text files. Engineers simply need to edit existing code to update policies, and with version control, they can revert to an older version if a new policy causes a problem. When one or more policies change, other team members can readily detect it.
8. Codified policies with comment explanations
By reviewing the code, all stakeholders may comprehend the background information and logic behind a policy. The ability to leave comments eliminates the need to contact engineers or security personnel.
Policy as code (PaC) - Conclusion
Policy as code (PaC) automates and improves an organization's total policy management, implementation, and configuration, resulting in more efficient, consistent, and reliable results. Policy as code (PaC) is a systematic technique for managing policies in software development that enables cooperation and automation. It adds to DevSecOps by improving the overall policy creation process.
Xcitium Secure Web Gateway protects enterprises from the complete range of web-borne cyber threats—known and unknown, without any IT footprint or security staff. Visit for more.

FAQ section
A: The term Policy as code refers to the use of code to manage and define specific rules and conditions. To make policy as code work, the team writes their policy through a particular programming language.
A: Among various benefits that can be extracted from the policy as code, some of which include version control, automation, testing, and sandboxing.
A: Compliance as code has a much broader sense within its specifications. It includes continuous monitoring for compliance along with the provision of specific steps for automated issue-solving mechanisms.
A: To reduce the time wasted on security audits and code reviews, the multi-cloud policy as code enables the codification of best practices on various domains such as security, operation elements, and compliances across all platforms hosted on a cloud.