Endpoint Security with
Patented ZeroDwell Technology
Traditional endpoint security solutions are detection-based, and thus cannot prevent new, unknown malware from entering your environment. However, we’ve developed an approach to safeguarding you from unknown malware. ZeroDwell proactively neutralizes unknown threats by virtualizing their attack vectors . They can do no damage while maintaining your business productivity.
Request Demo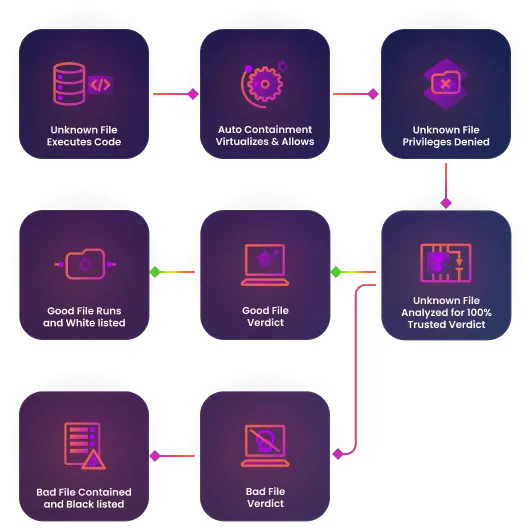
How It Works
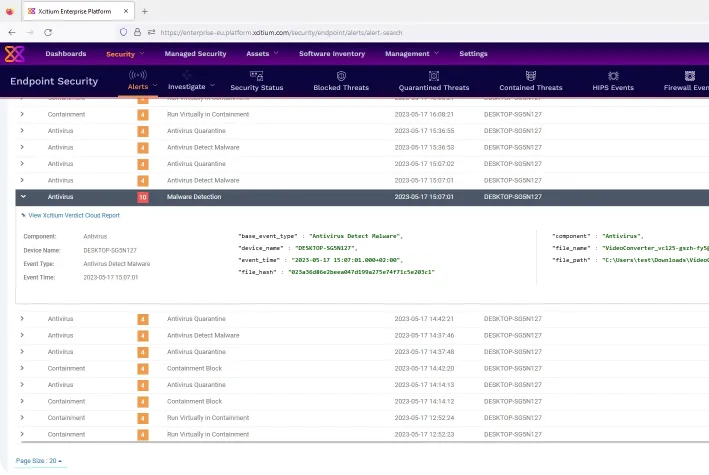
Neutralizing threats before they cause harm is crucial for maintaining security and business continuity. Xcitium's ZeroDwell technology offers a robust defense mechanism by isolating and virtualizing the attack vectors of potential threats in real-time. Our platform ensures that malware and other malicious activities are contained, preventing them from affecting your systems and data while allowing your operations to continue seamlessly.
Request DemoKey Features

Zero Trust Architecture
Implement a Zero Trust security framework where default-deny protection with default-allow performance is the standard, ensuring the security of your endpoints against unknowns.
Real-Time Threat Detection
Utilize advanced machine learning and artificial intelligence to detect and respond to threats in real-time. Our platform identifies and neutralizes threats before they can cause harm.
Advanced Malware Protection
Defend against known and unknown malware with our multi-layered approach. Xcitium Endpoint Security leverages behavioral analysis and heuristic scanning to prevent infections.

Xcitium Turns All Unknowns Into Known Good or Known Bad
Our advanced analysis engine swiftly identifies the nature of any file attempting to enter your network, ensuring that unknowns are no longer a vulnerability. This proactive approach means that every file is either safely allowed or instantly contained, giving you complete confidence that your endpoints are protected from both new and evolving threats.
Request Demo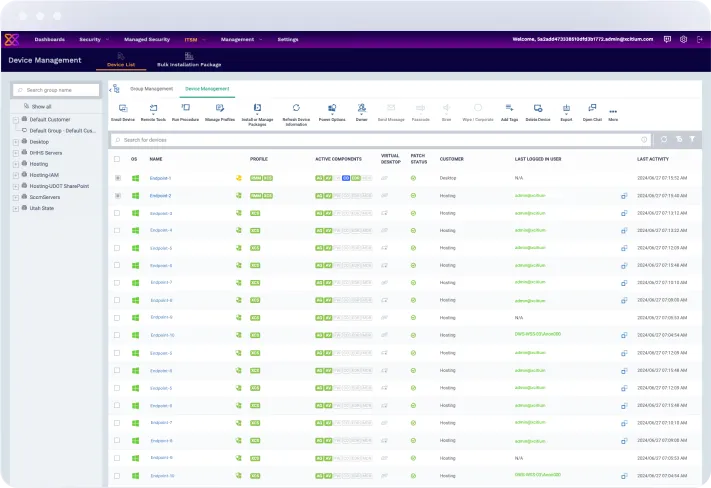
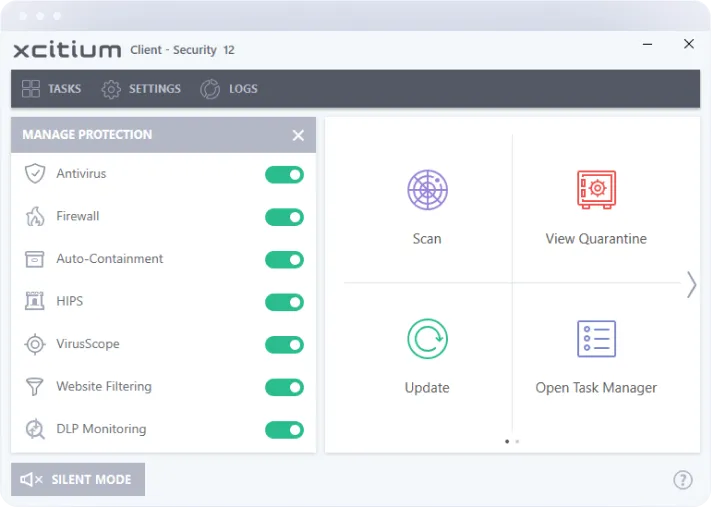
Comprehensive Device Management
Manage and secure all endpoints from a single, unified console. Simplify IT operations with centralized control over device policies, updates, and security configurations.
Automated Incident Response
Minimize the impact of security incidents with automated response capabilities. Xcitium Endpoint Security quickly contains and mitigates threats, reducing downtime and operational disruption.
Benefits
Solution
Why Choose Xcitium?
Xcitium exists to ensure that people can embrace technology fully, without the shadow of insecurity hanging over them. We’re here to give users the freedom to explore, create, and connect without fear. Whether it’s preventing unknown files from compromising systems or offering innovative approaches to endpoint protection, Xcitium’s technology is designed to foster confidence. We believe that by keeping the digital ecosystem secure, we’re directly contributing to human evolution—by enabling people to take full advantage of the tools that define our era.





