Microsoft is a global tech giant, and as such, it has a significant advantage when it comes to distributing new software. One of its many product development divisions is fixed on adapting Microsoft's existing applications and products for expansion into the cybersecurity market. Microsoft Defender (formerly Windows Defender), in particular, is Microsoft's cloud-native EPP + EDR detection and response platform for macOS, iOS, Android, and Linux endpoints.
Although feature parity can vary widely by operating system, and the tools used to deploy and manage Defender's endpoints are not yet fully unified, Microsoft is a monolith with an enormous presence. It is currently the largest cybersecurity company out there (as determined by revenue), and it has plans to further dominate the ever-evolving cybersecurity marketplace.
When choosing a cybersecurity solution, the question about whether bigger is better is highly relevant and might be worth considering when assessing Windows Defender for Endpoint Protection and its emerging advantages and disadvantages.

Windows Defender Endpoint Protection - Licensing
Microsoft used its Office 365 licensing model as a template for Microsoft Defender Endpoint Protection: each Microsoft Defender license is deployable to five devices.
To protect servers managed by Microsoft's Azure Security Center, Windows Defender can be included as part of Azure Defender. Although the client license allows deployment on up to five devices, the additional Azure license is applicable to one server only.
Here is the Microsoft Defender feature breakdown:
- Security:
- Attack Surface Reduction
- Microsoft Defender Antivirus (MDAV)
- Detection and Response | Alerting
- Microsoft Monitoring Agent (MMA)
- Supports Single Sign-On and Multi-Factor Authentication
- Office 365 apps, when purchased with a Microsoft 365 subscription
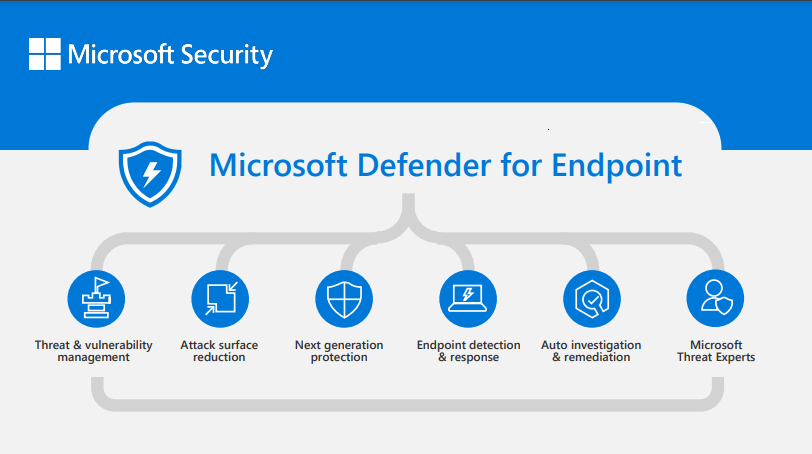
- Microsoft Defender and Azure Defender can optionally interface with XDR capabilities
- Azure Sentinel can optionally provide a cloud-native SIEM for context and attack correlations
- Vulnerability Management requires an add-on license
Microsoft Defender: OS-based Security
Microsoft introduced its first stable version of Windows Security endpoint protection platform (EPP) with its Windows 10 release (with Windows Defender AV). It has stepped through several evolutions since then. While building security right into an Operating System is a great advantage in principle, the reality is that Windows Security is integrated but not fully built into the OS, and it takes 8-16 months for most organizations to complete their Microsoft security rollout because Defender deployment is largely a manually-configured operation. Lengthy deployments can result in increased costs, and increased cyber risks to businesses during the interim.
Microsoft's integration of OS's, applications, and security capabilities is also a nontrivial pursuit that's going to take some time to realize. The fact that everyone uses Microsoft and its 365 business apps, including the US government and all of its military, means Microsoft can afford to take the time it needs to evolve robust security capabilities while customers gain improvements and fuller integrations in sequential rollouts. For example, even though Microsoft is ubiquitous, breaches do keep happening as they manage their security enhancements. Just earlier this year, U.S. officials using Microsoft-secured emails were hacked by Chinese tradecraft (msn.com), after which Microsoft announced newer security strategies to combat breaches going forward. Microsoft has also been posting advisories about Defender's outages, during which time customers are not protected.
Some experts argue that the reliance on one vendor's monopoly makes all of us more vulnerable to hacking and spying. In March 2023, the Russian military successfully exploited a vulnerability in Outlook that involved embedded malware with a persistent dwell time of over a year. The incident was concealed (many security vendors exhibit a similar lack of transparency regarding risk to their customers), but it was reported quietly in the cybersecurity trade press. (Newsweek May 16, 2023). So, as Microsoft Defender is promoted as the “epicenter for comprehensive endpoint security,” the cybersecurity industry recognizes that Defender is primarily a developing work in progress.
Microsoft Defender - Ease of Use
Ease of use is one of the most important requirements for all cybersecurity providers because there are so many attack methodologies, attack surfaces, and vulnerabilities to manage.
Microsoft Defender does come pre-installed on Windows 10 or 11 operating systems, so that is a distinct advantage, but many reviewers cite the need for extensive tuning.
The larger issue vis a vis “ease-of-use” is Microsoft Defender's reliance on several separate product consoles. Microsoft's marketing promotes management from one console, but the reality is they have not yet achieved unified security management. Defender usage still requires different consoles for different tasks, and different deployment methods for different operating systems. And users are required to navigate these variations on their own.
Also, Microsoft Defender has no built-in multi-tenancy capability. And the RBAC model is extremely limited. To cover the gap, Microsoft customers are forced to procure and manage additional tools to build custom workflows. For security management, customers are required to implement or adopt Microsoft Intune, and there are no native Linux security management capabilities.
Microsoft Defender Performance and Protection Stats
The Microsoft Defender product has repeatedly failed to deliver meaningful results in MITRE ATT&CK evaluations or AV-Lab's validation tests (AV Labs is an independent industry- recognized third-party testing and validation organization).
To get a deeper picture of Microsoft Defender performance statistics, it may be worthwhile to check out real-time detection stats for cybersecurity vendors https://threatmap.xcitium.com/ (request a demo to see Microsoft's stats). Missed detections continue to be an issue; Microsoft Defender allows “Unknowns” (files and objects with no known signature or hash) into customer environments by default (although they successfully block known-bad files and objects)--and everyone knows that malware and ransomware hides in Unknowns. To add complexity to the missed detections issue, their custom detection rules must execute during set time intervals (the minimum frequency of execution is every hour), so continuous monitoring is not available when custom rules are configured.
Another concern is the service limits and lockouts imposed on threat hunting queries. Advanced threat hunting is subject to tenant-level CPU quotas but customers are not informed beforehand. Microsoft Defender offers no information on how the service limits are calculated. But they do note that customers can be locked out of threat hunting queries for 15 minutes to 1 hour. When investigating alerts and performing forensics, these limits and lockouts might be a significant disadvantage for some customers.
Microsoft Defender, like so many detection-first solutions, reacts to threats and attacks. For example, when a malware or ransomware attack is inside a customer endpoint or environment and is performing reconnaissance to locate targeted data or assets, it can sometimes trigger Indicators of Compromise (IoCs), and only when these indicators are tripped can Microsoft Defender detect and react to the attack underway. This is not a proactive, zero trust technology that employs preventive, protection-first strategies to get ahead of attackers, which is where the cybersecurity industry must move.
Customers spend $262 billion annually on reactive cybersecurity solutions - in excess of a quarter of a trillion dollars per year - and yet they are not protected - breaches continue, daily. Microsoft Defender is reactive cybersecurity. Comparatively, proactive endpoint technology starts at the very beginning of the attack kill chain.
Microsoft Defender and Customer Support
Microsoft Defender for Endpoints provides varying tiers of support, each composed of sets of requirements that are complex and difficult to understand for each supported OS platform. And there is no support for legacy Windows systems, nor support for Linux on ARM or AIRS.
With regard to Microsoft Defender feature support, it tends to be so complex across platforms, the user community has had to create a public feature matrix to try to map available features to each OS platform to help users understand which features can be used in each OS environment (Check here). So Microsoft Defender's lack of operational transparency is a serious disadvantage.
Microsoft Defender is such a complex product that during a previous MITRE ATT&CK evaluation they had to pause the assessment process over a dozen times to make configuration changes in order to progress, and even then, they were only able to provide analytic detections for 98 of 109 required steps. An attacker only needs 1 inroad to enact a successful breach, and Microsoft Defender missed 11.
In the end, it is always recommended that customers ensure that all their criteria for endpoint security is met fully by a cybersecurity product under consideration, and that an analysis of the total cost of ownership (TCO) and return on investment (ROI) be part of the decision-making process, because, sometimes, licensing costs do not always represent the real costs associated with investing in an ineffective security solution. Sometimes bigger isn't always better when it comes to securing a business and its data.
Microsoft Defender vs Xcitium
Xcitium's lightweight, Zero-Dwell Containment proactively isolates all Unknowns at machine speed with patented virtualization technology that prevents attackers from accessing real data and resources. No other vendor pre-empts breaches with automated assessments of all Unknown files and file-less objects at runtime. This is proactive endpoint technology that truly starts at the very beginning of the attack kill chain.
Xcitium endpoint security is a prevention-first cybersecurity solution, providing end-to-end protection (EPP + EDR | MDR | XDR) with best-in-class zero trust technology that includes a 24/7 expert Security Operations Center (SOC) and elite human analysts who back up AI determinations and perform expert threat hunting and forensics. The Xcitium platform also provides consolidated remote management and IT tools without any hidden costs or complex configurations--all operated easily from one fully integrated, fully unified console.
Microsoft Defender customers: consider overlaying Xcitium ZeroDwell Containment as an add-on to your cybersecurity posture
Microsoft Defender does not claim to be able to prevent against payloads they cannot detect. But you can overlay Xcitium's pre-emptive EDR with automated ZeroDwell containment and manage it yourself. This way, any undetected payloads from Unknowns are contained proactively with virtualization and rendered harmless. Xcitium Advanced is a pre-emptive EDR solution that includes high-definition alerts and correlations without alert fatigue or a glut of false positives, because contained attacks are no longer threats.
Xcitium is one of only a very few cybersecurity vendors that can layer enterprise-wide MDR | XDR atop Microsoft Defender for endpoints, networks and clouds. If Microsoft Defender is your choice for cybersecurity, consider adding Xcitium's zero trust containment layer with managed SOC services atop Defender so you are not vulnerable to Zero Day payloads that will cause havoc. If your organization is committed to maintaining Microsoft Defender, you can better protect the organization by overlaying our world class, patented MDR solution that runs seamlessly aside Defender to pre-empt Unknown attacks and expand Defender's capabilities. Moreover, Xcitium never charges its MDR | XDR customers any Incident Response retainers or hourly fees.
- To see a demo of Xcitium's EDR, MDR, or XDR solutions and to learn how we can help strengthen your security posture, consolidate tools, and lower costs, contact us today for a 30-minute no-obligation consultation.
Are you interested in replacing your Microsoft Defender deployment?
If you are ready to move to a fully-integrated, next-gen cybersecurity solution for proactive end- to-end protection, we recommend:
- Xcitium Advanced (EDR)
- Xcitium Managed (MDR)
- Xcitium Completes (XDR)
Each option is deployed with innovative ZeroDwell containment.
Xcitium Advanced provides pre-emptive EDR and the demonstrated ability to make threat management much easier for your IT team, or you could opt to allow our world class cybersecurity experts to manage all your cybersecurity for you with Xcitium MDR or XDR capabilities.
- Please do join us to see a demo of Xcitium's EDR, MDR, or XDR solutions and to learn how we can pre-empt attacks and improve your security profile enterprise-wide: contact us today for a 30-minute no-obligation consultation.
Are you looking for a new cybersecurity vendor?
Xcitium delivers robust pre-emptive auto-containment cybersecurity, plus continuous enterprise- wide monitoring, detection, actionable visibility, and remediation capabilities that help organizations reduce risk and prevent known and unknown attacks, without any disruption of business operations or productivity.
Xcitium's security experts are available to assess your current environment and show how our patented ZeroDwell containment, advanced endpoint protection, and 24/7/365 Managed SOC services can optimize your cybersecurity posture. In addition, you will never have to worry about unpredictable incident response (IR) fees, because Xcitium is one of the only vendors that does not require a costly IR retainer or charge hourly IR fees from its MDR/XDR customers.
Don't wait for an incident - schedule a demo today to start fortifying defenses and unlocking the full potential of your security infrastructure with Xcitium.
And remember: Xcitium ZeroDwell Containment works side-by-side with existing security infrastructure, including Microsoft.
- Talk with us about Xcitium's EDR, MDR, or XDR solutions to learn how we can help strengthen your security posture, consolidate tools, and lower costs: contact us today for a 30-minute no-obligation consultation.
