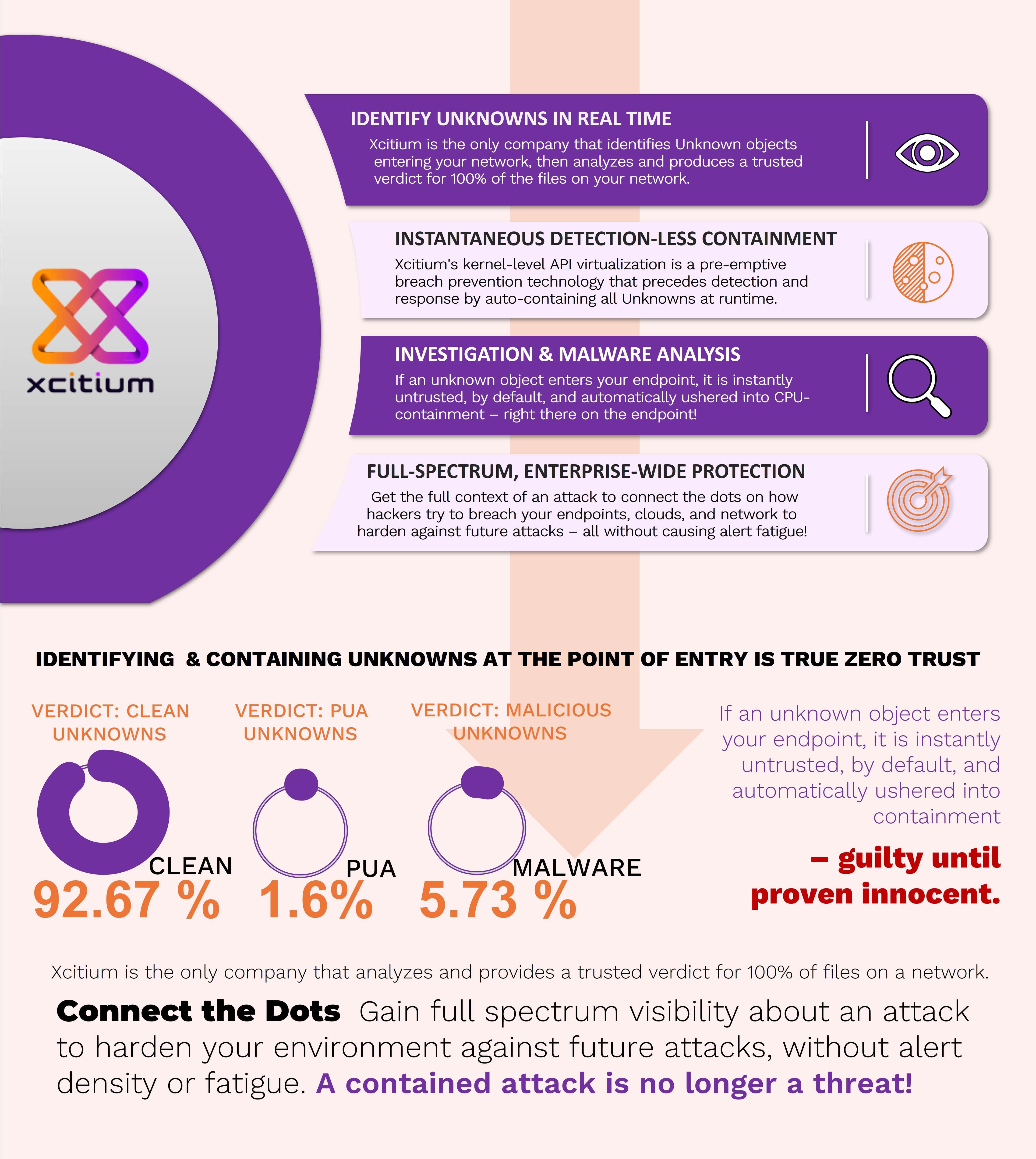
WHAT IS EDR SECURITY?
Attackers are always looking for new strategies to defraud and damage organizations. Your employees' off-site devices can be one of the entry points used to penetrate your network. With remote working now a common practice around the world, it's no surprise that endpoints are getting more and more vulnerable. Having an uneven endpoint security detection layer between your network and attackers can put your critical assets at risk. For this reason, your response security teams need to put proper endpoints cybersecurity protection measures like EDR in place. After all, malicious hackers are constantly lurking to take advantage of your existing detection vulnerabilities.
What is Endpoint Detection & Response? - EDR Security Definition
Aside from the usual firewalls and antivirus software, your endpoint detection response EDR security teams can make use of Endpoint Detection and Response (EDR). This tool covers EDR cyber threat hunting, prevention, and detection of malware and other cyberattacks in your network through a real time response. Efficient endpoint detection response EDR solutions can recognize suspicious behaviors and actively respond to threats in your endpoints.
WHAT ARE THE TOP EDR SECURITY SOLUTIONS?
To assist your IT endpoint security teams in proactively mitigating EDR cyber threats with a smart security response, EDR solutions provide the following features:
Detection
Detecting threats is a core capability of an endpoint EDR solution. solution. An advanced threat will likely attack you, so your endpoint EDR solutions must be prepared when they come to evade your front-line defenses. Upon entering your environment, your IT security system should be able to detect accurately the EDR cyber threat to contain and eliminate it in real time. This can be challenging especially when you're dealing with endpoints sophisticated malware which can be sneaky. They may act as harmless at first but gradually turn into malicious activity malware soon after they cross the point of entry. The endpoint EDR solutions, thus, helps greatly in such scenarios.
EDR endpoint detection response solution continuously analyzes files to flag down those showing signs of malicious behaviors in real time. If a file initially passes as safe but a few days later begins to show ransomware activity, the endpoints software can still detect the file and alert your endpoint security teams so they can take action.
You should remember that endpoint EDR is only as good at detecting files as the cyber that influences it. Response EDR cyber threat intelligence uses big data, machine learning capabilities, and advanced file analysis for running detection to sort out threats. The more powerful your cyber threat intelligence is, the more likely your EDR software can spot the risk.
Containment
After giving an endpoint detection response solution, an endpoint EDR program can contain a malicious file to avoid infecting legitimate processes, applications, and users. Segmentation can be beneficial in your organization, allowing your security teams prevent a lateral movement of advanced threats in your network. Along with EDR protection, this can help contain malicious files before they even wreak havoc to your system. One example of a tricky issue to remove is ransomware. Once it has encrypted the information, your endpoint security teams must fully contain it to reduce the damages it can cause.
Investigation
After detecting and containing the malicious file, the endpoint detection response EDR solution should be further investigated. If the file was able to pass through your defenses the first time, it only means that there's a vulnerability present. It could be possible that the threat intelligence failed to detect it as it has never encountered this kind of threat before. Another reason could be the outdated application. Without properly investigating, your security teams won't get to the root of the problem. As a result, your network might just experience the same hazards again
During the investigative and detection process, sandboxing is necessary. With a sandbox, you can test a suspicious file to observe its behavior. The rest of your network is isolated and protected from the negative effects brought about by the things operating in the sandboxed environment.
Within this kind of environment, the EDR endpoint security tool can determine the nature of the file without putting your whole system at risk. After assessing, it can communicate the endpoint detection response of findings with the EDR cyber threat coping strategies so new strategies can be adapted to better prepare for future situations.
Elimination
Aside from detecting, containing, and investigating, The EDR detection solution can also eliminate threats. After reviewing endpoint security incidents, your endpoint EDR solutions must enable the security teams to immediately take action to respond to the incident in real time. Without doing this, you just continue, knowing that your system is compromised. To eliminate vulnerabilities properly, your EDR endpoint detection solution requires good visibility to determine where files originate, what data and applications they interacted with, and if the file has been replicated.
Visibility is needed to see the entire timeline of a file. It is not as simple as deleting the file you've monitored. When you eliminate a file, you may have to remediate various parts of the network automatically. Because of this, the EDR endpoint detection response solutions should provide actionable data on the file's whole lifecycle. If the EDR solution has retrospective abilities, the actionable data can remediate and revert the systems to how they were before infection.
Conclusion - Xcitium's EDR Security Solution
As cyberattacks continue to increase and become sophisticated, more and more people see the significance of adopting good endpoint detection response EDR solutions. Afterall, EDR provides visibility into your endpoints so you can respond quickly to malicious actions.
For comprehensive endpoint protection solutions, choose Xcitium EDR. We can help you stay on top of your IT environment so your endpoint security teams can fend off threats that compromise your system. Contact us now!