What is Secure Access Service Edge (SASE)?
Secure Access Service Edge, commonly abbreviated as SASE (pronounced "sassy"),is a transformative framework that merges networking and security into a single, cloud-delivered solution. Introduced by Gartner in 2019, SASE addresses the evolving needs of modern enterprises as they shift toward distributed workforces, cloud-based applications, and heightened cybersecurity threats. Unlike traditional models that rely on centralized data centers and perimeter-based security, SASE leverages a distributed, cloud-native architecture to deliver seamless connectivity and protection wherever users and devices are located.
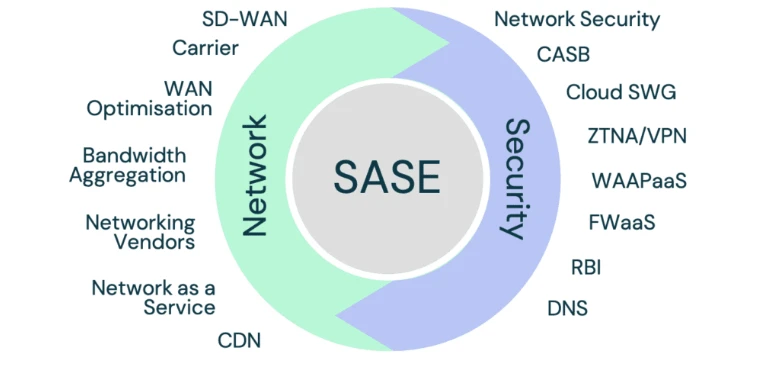
At its core, SASE integrates two primary domains: networking and security. On the networking side, it incorporates Software-Defined Wide Area Networking (SD-WAN),which optimizes traffic across multiple connections—such as MPLS, broadband, or 5G—ensuring low latency and high performance for cloud applications. On the security side, SASE bundles a suite of tools like firewalls-as-a-service (FWaaS),secure web gateways (SWG),zero trust network access (ZTNA),and data loss prevention (DLP). By combining these capabilities into a unified platform, SASE eliminates the need for multiple standalone solutions, reducing complexity and improving efficiency.
The magic of SASE lies in its cloud-centric design. Rather than routing traffic through a physical data center, SASE uses a global network of Points of Presence (PoPs) to process and secure data closer to the user. This edge-based approach minimizes latency, enhances user experience, and scales effortlessly to meet growing demands. For example, a remote employee accessing a cloud app from a coffee shop benefits from the same level of security and performance as someone in a corporate office—all without the backhauling delays of traditional VPNs.
SASE also embraces a zero trust security model, meaning it verifies every user, device, and connection before granting access, regardless of location. This is a stark contrast to legacy systems that often assumed trust within the network perimeter—a risky assumption in today’s borderless digital world. By enforcing strict identity-based policies, SASE protects against threats like malware, phishing, and unauthorized access, making it ideal for hybrid work environments and cloud migrations.
In essence, Secure Access Service Edge is the future of enterprise networking and security. It offers businesses a flexible, cost-effective way to support digital transformation while safeguarding sensitive data. Whether you’re a global corporation or a growing startup, SASE provides the agility and resilience needed to thrive in a cloud-first era.
Core Components of SASE
Secure Access Service Edge (SASE) is built on a foundation of integrated technologies that combine networking and security into a cohesive, cloud-native framework. These core components work together to deliver fast, secure, and scalable access to applications and data, regardless of where users or resources are located. Understanding these elements is key to grasping how SASE transforms enterprise IT. Let’s break them down.
First, Software-Defined Wide Area Networking (SD-WAN) serves as the networking backbone of SASE. SD-WAN optimizes connectivity across multiple transport methods—like MPLS, broadband, or 4G/5G—by intelligently routing traffic based on real-time conditions. This ensures low latency and high performance for cloud-based applications, such as Microsoft 365 or Salesforce, even in remote or branch office scenarios. Unlike traditional WANs, SD-WAN’s software-driven approach allows for centralized management and dynamic adjustments, making it a perfect fit for SASE’s distributed architecture.
Next, cloud-delivered security services form the protective layer of SASE. This includes a suite of tools designed to safeguard data and users at the edge. Firewalls-as-a-Service (FWaaS) replace physical appliances with scalable, cloud-based firewalls that inspect traffic and block threats. Secure Web Gateways (SWG) filter internet-bound traffic to prevent malware and enforce browsing policies. Zero Trust Network Access (ZTNA) ensures that only authenticated and authorized users or devices can connect to resources, applying a “never trust, always verify” philosophy. Together, these tools eliminate the need for on-premises hardware and provide consistent security across all locations.
Another critical component is the cloud-native architecture itself. SASE operates through a global network of Points of Presence (PoPs),strategically placed near users and applications. These PoPs handle both networking and security functions, reducing latency by processing traffic at the edge rather than backhauling it to a central data center. This distributed model scales effortlessly, supporting everything from a single remote worker to a multinational enterprise.
Finally, identity and policy management ties it all together. SASE relies on user and device identities—rather than IP addresses—to enforce access controls. This granular approach, often powered by artificial intelligence and machine learning, adapts policies in real time, enhancing security without sacrificing usability.
In summary, the core components of SASE—SD-WAN, cloud security services, edge delivery, and identity-driven policies—create a unified platform that simplifies IT, boosts performance, and strengthens defenses. It’s a modern solution for a modern world.
SASE vs Traditional Networking and Security Models
Secure Access Service Edge (SASE) represents a paradigm shift from traditional networking and security models, which were designed for a world where data and users stayed within a fixed corporate perimeter. As businesses adopt cloud computing, remote work, and mobile devices, these legacy systems struggle to keep up. Comparing SASE to traditional setups reveals why it’s becoming the go-to solution for modern enterprises.
Traditional networking often relies on MPLS-based WANs and hub-and-spoke architectures. In this model, traffic from branch offices or remote users is routed through a central data center for processing and security checks. While this worked when applications lived on-premises, it creates bottlenecks for today’s cloud-based tools like Zoom or AWS. Users experience latency as data travels long distances, and IT teams face complex management of physical circuits. SASE, by contrast, uses Software-Defined WAN (SD-WAN) to intelligently route traffic over multiple connections—broadband, 5G, or MPLS—via a distributed network of cloud-based Points of Presence (PoPs). This edge-driven approach slashes latency and scales dynamically, aligning with the needs of a decentralized workforce.
On the security front, traditional models depend heavily on perimeter-based defenses, such as on-site firewalls and VPNs. These assume that anything inside the network is trustworthy—an outdated notion in an era of sophisticated cyber threats and remote access. VPNs, for instance, grant broad network access once a user logs in, leaving vulnerabilities if credentials are compromised. SASE flips this script with a zero trust security model, verifying every user, device, and connection before granting access to specific resources. Integrated tools like Firewalls-as-a-Service (FWaaS) and Secure Web Gateways (SWG) apply consistent protection at the edge, eliminating the need to backhaul traffic to a data center.
Cost and complexity also set SASE apart. Traditional setups require stacks of hardware—routers, firewalls, load balancers—plus separate management for each. This drives up expenses and slows deployment. SASE consolidates these functions into a single cloud-delivered platform, reducing overhead and simplifying IT operations. For example, a company expanding to new regions no longer needs to ship appliances; it just leverages SASE’s global PoPs.
In short, SASE outperforms traditional networking and security models by offering agility, scalability, and robust protection tailored to a cloud-first world. While legacy systems linger, SASE is clearly the future for enterprises embracing digital transformation.