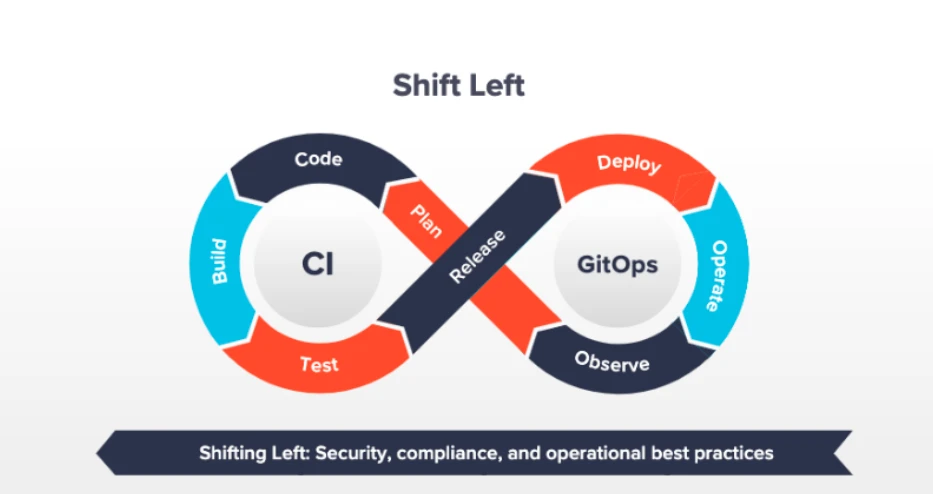
What is Shift Left Security?
Shift Left Security is a proactive cybersecurity approach that integrates security measures early in the software development lifecycle rather than treating security as a final step before deployment. Traditionally, security testing and vulnerability assessments were conducted at the end of the development process, often leading to delays, costly fixes, and increased risk exposure. Shift Left Security moves security practices to the beginning of the development pipeline, embedding security testing and risk mitigation into coding, build, and testing phases.
By incorporating security early, developers and security teams can identify vulnerabilities and address them before they become major risks. This reduces the likelihood of deploying insecure applications and prevents security bottlenecks that can slow down the development process. Shift Left Security aligns with the DevSecOps model, which emphasizes integrating security into DevOps workflows to ensure continuous security monitoring and compliance.
One of the primary benefits of Shift Left Security is the early detection of vulnerabilities. Since security testing is performed throughout development, security flaws such as insecure code, misconfigurations, and access control weaknesses can be identified and remediated before they make their way into production. This proactive approach significantly reduces the cost of fixing security issues, as addressing vulnerabilities in the coding stage is far less expensive than applying security patches after deployment.
Shift Left Security relies on automation to enhance security without slowing down development. Security tools such as static application security testing (SAST),dynamic application security testing (DAST),and software composition analysis (SCA) are integrated into CI/CD pipelines to scan for vulnerabilities in real time. These automated security checks ensure that code is continuously tested for security risks without requiring manual intervention, improving efficiency and reducing human error.
Another critical aspect of Shift Left Security is developer empowerment. Instead of security being solely the responsibility of dedicated security teams, Shift Left encourages developers to take an active role in writing secure code. Security training, code review best practices, and secure coding guidelines help developers identify and prevent vulnerabilities at the source. This cultural shift promotes security awareness across development teams and fosters collaboration between security and engineering departments.
Shift Left Security also enhances regulatory compliance. Many industries require organizations to follow strict security and data protection standards such as GDPR, HIPAA, and PCI-DSS. By embedding security into development workflows, organizations can ensure that compliance requirements are met from the outset, reducing the risk of regulatory violations and penalties.
As cyber threats continue to evolve, organizations need a proactive approach to security. Shift Left Security minimizes risk, strengthens software resilience, and ensures that security is a core component of the development process. By adopting Shift Left principles, businesses can build more secure applications while maintaining agility and speed in software delivery.
Key Benefits of Implementing a Shift Left Security Approach
Implementing a Shift Left Security approach provides organizations with a proactive defense against cyber threats by integrating security early in the software development lifecycle. Instead of addressing security issues at the end of development or after deployment, Shift Left Security embeds security practices throughout coding, testing, and CI/CD processes. This approach enhances software security while also improving efficiency, reducing costs, and ensuring compliance. Below are the key benefits of adopting a Shift Left Security strategy.
One of the most significant advantages of Shift Left Security is the early detection and remediation of vulnerabilities. Traditional security models often identify vulnerabilities late in the development cycle, requiring costly and time-consuming fixes. By shifting security left, organizations can catch security flaws during the coding and testing phases, allowing developers to resolve issues before they become critical. Fixing vulnerabilities early reduces security risks and prevents security incidents from impacting production environments.
Another major benefit is the reduction in remediation costs. Research shows that fixing security vulnerabilities in production can be up to 100 times more expensive than addressing them during development. When security testing is embedded throughout the software lifecycle, organizations can minimize costs associated with emergency patches, security breaches, and post-deployment remediation efforts. This cost-effectiveness makes Shift Left Security a crucial investment for any development team.
Shift Left Security also helps accelerate software delivery by integrating security into DevOps workflows. Traditional security testing methods often create bottlenecks that slow down the deployment process. By automating security testing with tools like static application security testing (SAST),dynamic application security testing (DAST),and software composition analysis (SCA),development teams can maintain speed without compromising security. Automated security testing ensures that vulnerabilities are detected and addressed continuously, reducing delays in software releases.
Another key advantage is improved compliance and regulatory adherence. Many industries require organizations to meet strict security and data protection standards such as GDPR, HIPAA, and PCI-DSS. By implementing Shift Left Security, organizations can ensure that compliance measures are met throughout development, reducing the risk of non-compliance penalties. Continuous security monitoring and automated compliance checks help organizations maintain adherence to industry regulations.
Shift Left Security also fosters a culture of security awareness among developers. By empowering developers with security training, secure coding best practices, and access to security tools, organizations can reduce reliance on dedicated security teams and promote a shared responsibility for cybersecurity. When developers take an active role in security, they write more secure code, reducing the likelihood of introducing vulnerabilities into the software.
Additionally, Shift Left Security enhances software resilience against emerging threats. Cyber threats evolve rapidly, and organizations need a proactive security approach to stay ahead. By embedding security into every stage of development, Shift Left Security strengthens applications against sophisticated attack techniques, ensuring that security is continuously reinforced rather than being treated as an afterthought.
Overall, adopting a Shift Left Security approach helps organizations build more secure, efficient, and compliant software. By identifying vulnerabilities early, reducing costs, streamlining development, and fostering a culture of security, Shift Left Security becomes a critical strategy for modern software development teams.
Shift Left Security vs. Traditional Security Approaches
Shift Left Security represents a fundamental shift from traditional security approaches by integrating security early in the software development lifecycle rather than addressing it at the final stages. Traditional security models often treat security as a separate phase, typically conducted just before deployment or after software is already in production. This reactive approach can lead to delays, increased remediation costs, and heightened security risks. In contrast, Shift Left Security embeds security into the development process from the start, making it a proactive and cost-effective approach. Below is a comparison of Shift Left Security and traditional security approaches, highlighting their key differences and benefits.
One of the primary distinctions between Shift Left Security and traditional security is when security measures are applied. In traditional security approaches, security assessments, vulnerability scans, and penetration testing occur toward the end of the development cycle or even post-deployment. This means that security issues may only be identified after the software is complete, requiring significant rework and delaying releases. In contrast, Shift Left Security ensures that security testing happens throughout development, from the initial coding phase to continuous integration and testing. By detecting vulnerabilities early, developers can address them before they become major risks.
Another critical difference is the cost and effort required for remediation. In traditional security models, fixing vulnerabilities late in the development process is costly and time-consuming. A security flaw discovered during production may require significant code rewrites, delaying project timelines and increasing expenses. Shift Left Security minimizes these costs by identifying and resolving vulnerabilities at the source, often during coding or early testing. Studies show that fixing security issues during development can be up to 100 times less expensive than fixing them in production.
Automation and integration also set Shift Left Security apart from traditional approaches. Traditional security testing often relies on manual reviews and security audits, which can slow down the development cycle and create bottlenecks. Shift Left Security, on the other hand, leverages automated security tools such as static application security testing (SAST),dynamic application security testing (DAST),and software composition analysis (SCA). These tools are integrated directly into CI/CD pipelines, allowing security checks to run automatically with every code change. This automation reduces human error, improves efficiency, and ensures security is a continuous process rather than a final checkpoint.
Another major advantage of Shift Left Security is developer involvement in security. In traditional security models, security is typically the responsibility of dedicated security teams, often separate from developers. This siloed approach can lead to delays in addressing vulnerabilities and create friction between development and security teams. Shift Left Security encourages a security-first mindset by making developers active participants in securing code. Through security training, code reviews, and automated security scans, developers gain the skills and tools needed to write more secure code from the beginning.
When it comes to compliance and regulatory adherence, Shift Left Security provides a more efficient way to meet industry security standards. Traditional security models often focus on compliance audits after software development is complete, leading to rushed fixes and increased risk of non-compliance. With Shift Left Security, compliance checks are integrated throughout the development lifecycle, ensuring that security policies are consistently enforced and reducing the risk of violations.
Finally, resilience against evolving threats is a key advantage of Shift Left Security over traditional security approaches. Cyber threats are constantly evolving, and organizations must stay ahead of attackers. Traditional security models often fail to address new vulnerabilities in a timely manner, leaving applications exposed until the next scheduled security review. Shift Left Security, by continuously testing for security risks, allows organizations to proactively adapt to emerging threats and maintain a strong security posture.