Password spraying (or a Password Spray Attack) occurs when an attacker attempts to access multiple accounts on the same domain using common passwords. An attacker might possibly access hundreds of accounts in a single attempt by using a list of common weak passwords, such as 123456 or password1.
Cybercriminals can get access to many accounts at the same time, granting them access to commercial or personal accounts as well as personal information. If a cybercriminal gains access to even one-third of your company's accounts with Password Spraying, they could gain access to the following:
- Bank information
- Personal information on employees
- Benefits information, such as account numbers
- Sensitive company data
- Product information
- Trade secrets
- Other login credentials
Common indications of a password spraying attack include the following:
- An unusually high volume of login activity over a small period of time
- Sudden failed login attempts by active users
- unusual login activity from nonexistent or inactive accounts
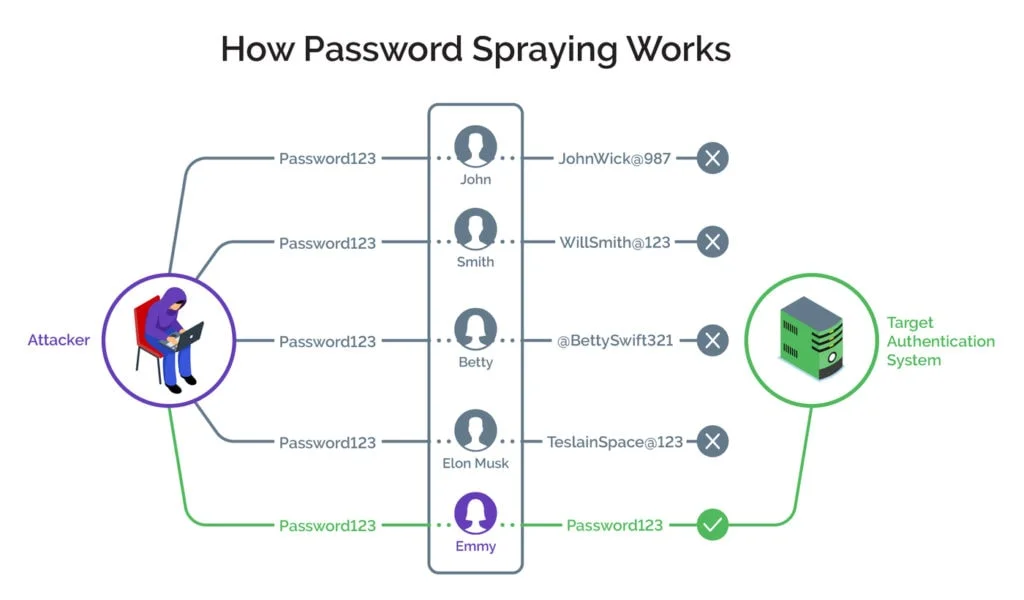
How is a Password Spraying Attack Executed?
A password spraying attack is carried out in two stages. An attacker obtains a list of users and then attempts logins using the same password across all accounts. The attacker repeats the process with different passwords until the attacker has account and system access by breaching the target authentication systems.
Why Is Password Spraying Regarded as a Brute Force Attack?
Password spraying is a type of brute force attack that differs from regular brute force attacks in that it attempts to guess a password for a single account. However, it still employs the widespread trial-and-error technique that is characteristic of a brute-force attack. Because it guesses passwords across multiple accounts until it finds a match, a password spray assault is regarded as brute force.
How is Password Spraying Impacts Business?
A password spraying attack can affect various levels of a business. The attack could target consumer accounts in order to utilize their credentials on other websites. Password spraying can also be used to access a new employee's business account. Attackers may go ahead with privilege escalation using stolen credentials in order to get more access to your company's confidential information. A successful password spraying attack makes you more exposed to other types of attacks in the future.
How Can Password Spraying Impact the Bottom Line of a Business?
If successful, a password spray attack can inflict considerable financial harm to a company. An attacker using seemingly legitimate credentials can gain access to your financial accounts and use them to make fraudulent purchases. Malicious companywide emails could bring the day's productivity to a huge halt. An attacker taking over a company account could cancel transactions, change the delivery date of services, or steal confidential information. Recovery from a Password Spraying attack typically takes two to four weeks but might take months in severe instances.
How Does a Password Spraying Attack Impact Your Customer Base?
A loss of client confidence is one of the most serious impacts of a password spraying attack on a company. Customers are less likely to believe that their data and information are safe with you if your company is compromised by a brute force attack of any kind. They may take their business elsewhere, resulting in additional financial loss.
Another potential risk of effective password spray attacks is that the hacker will try to phish your credentials. An attacker's email to a customer may cause financial harm to both you and the other party, as well as further reputational harm.
How to Prevent Password Spraying?
For Personal UsersUse Multi-Factor AuthenticationPassword Spraying Attack requires additional credentials to enter your accounts and notifies you of attempted logins. Increasing the variety of your 2FA/MFA requirements might add an extra layer of security.
Limit using common passwordsMake each account's password unique and complicated, and never reuse passwords. A password manager can assist you in creating stronger, more unique passwords, storing them securely, and integrating them with third-party authentication software.
As a Business
Take the following precautions to protect your company and its employees:
- Implement multi-factor authentication and security questions on enterprise portals.
- CAPTCHAs can be used to prevent bots from logging into accounts using stolen credentials.
- Use VPNs for your staff to mask IP addresses and make it far more difficult for an attacker to pinpoint your company's real IP addresses.
- Implement a robust cybersecurity strategy at your organization that emphasizes the usage of unique, complicated passwords for each account.
- Implement company-wide training for all employees about password spraying, other cybersecurity issues, and the importance of strong passwords. Include information on how to generate stronger passwords, identify dangers, and what to do if you think your account has been compromised.
Stay Protected all the Time - Conclusion
Because common passwords are often compromised, the risk of password spraying has increased more than ever. More than 65% of internet users use the same password for many or all of their accounts. It's easy to understand why password spraying is so effective—a few people using common passwords may put an entire firm at risk.
And so, it is crucial to have strong passwords in place to prevent data breaches. After all, you don't want hackers using advanced cracking techniques to acquire your company's confidential credentials. Enterprise Password Management from Xcitium is a complete solution that gives organizations secure and efficient access to important systems. Visit for more.
FAQ section
A: The term password spraying refers to when an attacker uses common passwords to access more than one account on any domain. This is also known as Password Spray Attack.
A: Password spraying success rate is around to be 1% for all those accounts which doesn't have password protection installed.
A: With the help of Multi-factor authentication, your password alone would be sufficient enough to provide access to the device. Passwordless infrastructure is usually regarded as the best option to completely secure from password spraying.
A: Password spraying is regarded as one of the most common cyberattacks used to compromise accounts. By Microsoft, around 3rd of all accounts get compromised through password spray attacks.