Managed Detection & Response (MDR) with No Cost Incident Response
Our managed detection and response (MDR) technologies and security experts service your business remotely to keep you protected so you can focus on your enterprise. Offload day-to-day security event triage and analysis so your team can focus on organizational needs.
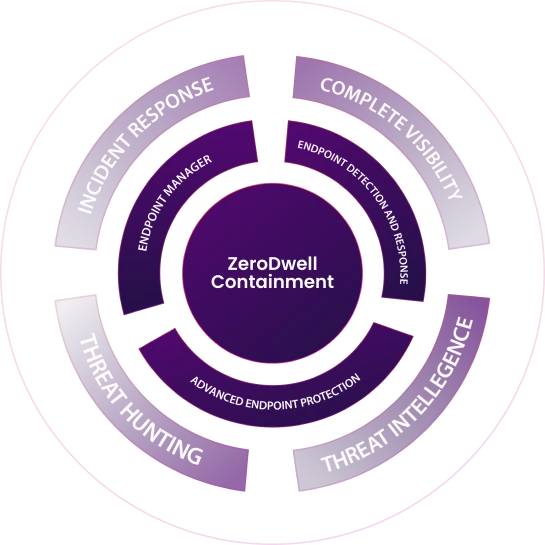
How It Works
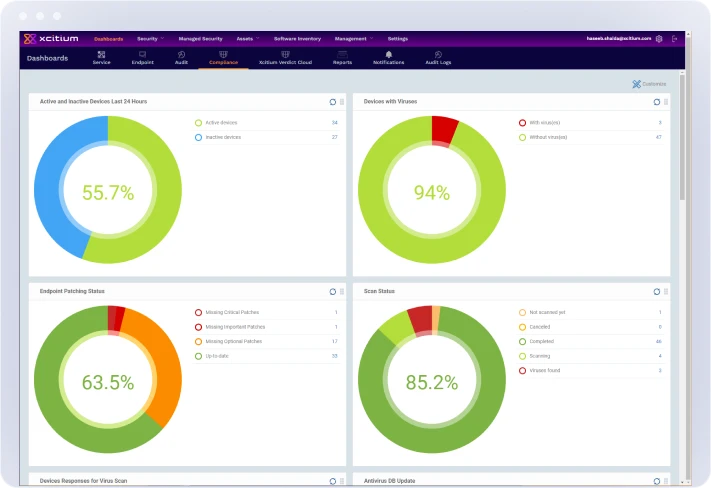
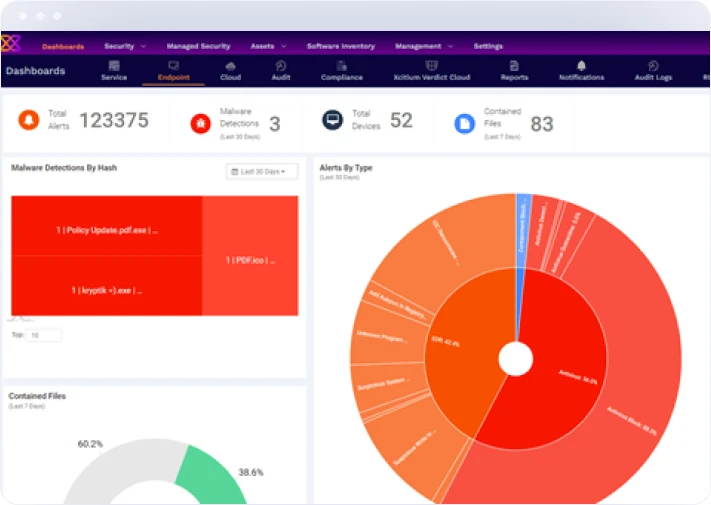
Receive detailed reporting on threat activity affecting your environment. Get high fidelity notifications on file-less attacks, advanced persistent threats, and privilege escalation attempts. Our experts closely monitor your environment 24x7x365 and respond regardless of your time zone or location.
Key Features

Continuous monitoring and in-depth analysis of network traffic and endpoint activities.
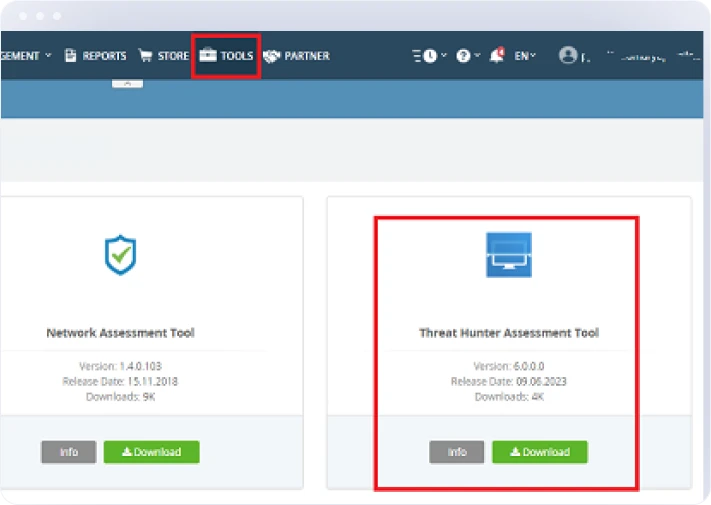
Proactive Threat Hunting
Identifies and investigates potential threats before they can cause harm.
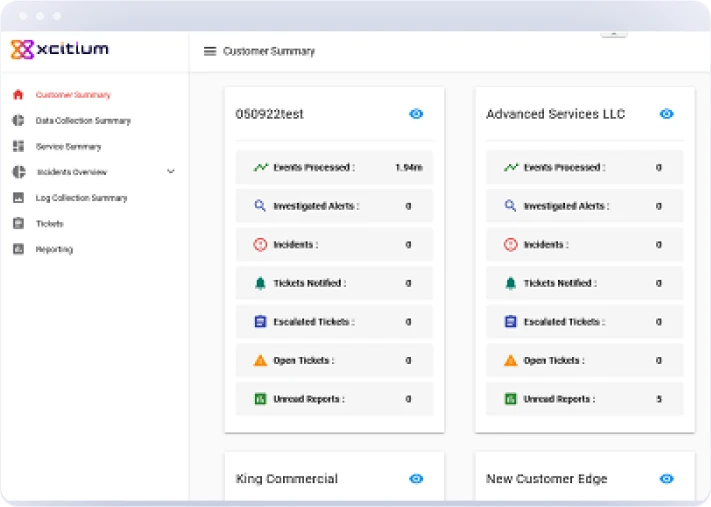
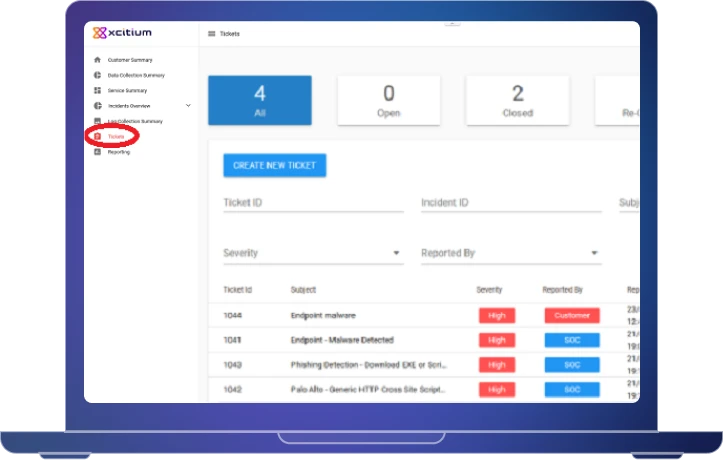
Incident Response and Remediation
Rapid response to security incidents with detailed remediation steps to minimize impact.
Security Information & Event Management (SIEM)
Centralized collection, analysis, and correlation of security data for comprehensive threat detection.
Advanced Threat Intelligence
Integration of global threat intelligence to enhance detection and prevention capabilities.
Behavioral Analytics
Detects anomalies and unusual activities through advanced behavioral analysis techniques.
Benefits
Solution
Why Choose Xcitium?
Xcitium is a leader in cybersecurity, offering innovative solutions to protect against the most advanced threats. Our endpoint security platform combines cutting-edge technology with expert support, ensuring your business stays secure in a constantly evolving threat landscape. Trust Xcitium to safeguard your endpoints and protect your business.





