Key Differences Between Malware and Viruses
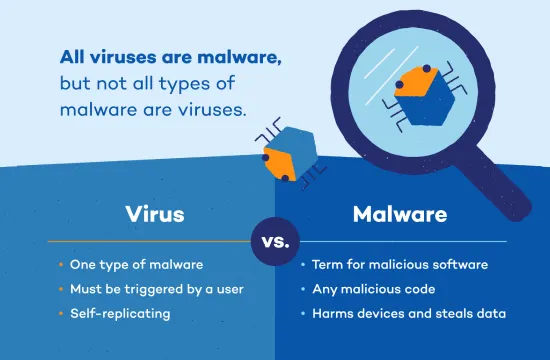
Malware and viruses are often confused, but they have distinct characteristics that set them apart. Malware is a broad term that encompasses any malicious software designed to harm, exploit, or compromise a system. This includes viruses, worms, ransomware, spyware, adware, and Trojans. A virus, on the other hand, is a specific type of malware that infects files and spreads by attaching itself to legitimate programs or documents. Understanding these key differences is essential for effective cybersecurity and threat prevention.
One major difference between malware and viruses is how they spread. Viruses require human action to propagate, meaning they only spread when a user unknowingly executes an infected file or program. For example, opening an infected email attachment or downloading compromised software can activate a virus. Malware, however, can spread through various means, including malicious websites, phishing attacks, unpatched software vulnerabilities, and even removable media like USB drives. Some forms of malware, such as worms, can replicate and spread autonomously without user interaction.
Another critical difference is how they operate. Viruses work by injecting their malicious code into host files, which means they remain dormant until the infected file is executed. Once activated, a virus can corrupt, delete, or modify files, potentially rendering a system unusable. Other types of malware, such as ransomware, encrypt files and demand payment for decryption, while spyware silently monitors user activity to steal sensitive data. Unlike viruses, many malware types do not require host files and can run independently, making them more versatile and harder to detect.
The level of damage caused by viruses and malware also differs. While viruses primarily target files and software, malware can go beyond file corruption to compromise entire networks, steal credentials, or even take control of systems remotely. Cybercriminals use different malware variants to achieve specific goals, such as financial fraud, espionage, or large-scale cyberattacks. Some modern threats combine multiple forms of malware, making them more difficult to identify and remove.
Preventing infections requires different security measures. Traditional antivirus programs are effective at detecting and removing viruses but may not be sufficient against advanced malware threats. Comprehensive cybersecurity solutions, such as endpoint protection, firewalls, and behavior-based detection, are necessary to combat modern malware attacks. Implementing best practices like software updates, multi-factor authentication, and Zero Trust security can further reduce the risk of infections.
In summary, while all viruses are malware, not all malware are viruses. Understanding the distinctions between them helps individuals and organizations adopt the right security strategies to protect their systems from evolving cyber threats.
Common Types of Malware Beyond Viruses
Malware is an umbrella term for various types of malicious software designed to infiltrate, damage, or exploit systems. While viruses are one of the most well-known forms of malware, many other types pose significant threats to individuals and organizations. Understanding the different types of malware beyond viruses helps in developing stronger cybersecurity defenses and mitigating risks more effectively.
One of the most dangerous types of malware is ransomware, which encrypts files or entire systems and demands payment for decryption. Cybercriminals use ransomware to target businesses, hospitals, and government agencies, often paralyzing operations until the ransom is paid. Unlike viruses, which rely on file execution to spread, ransomware typically infiltrates systems through phishing emails, software vulnerabilities, or malicious downloads.
Worms are another type of malware that differ significantly from viruses. Unlike viruses, worms do not need a host file to replicate; they can spread autonomously across networks without user intervention. Worms exploit vulnerabilities in software or operating systems, allowing them to propagate rapidly and cause widespread damage. Some worms carry additional malicious payloads, such as backdoors that enable hackers to gain remote access to infected systems.
Trojans disguise themselves as legitimate software to deceive users into installing them. Once inside a system, a Trojan can perform a variety of malicious activities, such as stealing credentials, creating backdoors for hackers, or deploying additional malware. Trojans do not self-replicate like viruses or worms, but they are commonly used as an entry point for more advanced cyberattacks.
Spyware is designed to secretly monitor user activity and collect sensitive information, such as login credentials, banking details, and browsing habits. Often bundled with seemingly harmless applications, spyware operates in the background without the user’s knowledge. It can be used for identity theft, corporate espionage, or government surveillance.
Adware is a less harmful but still intrusive type of malware that bombards users with unwanted advertisements. While some adware is legitimate and revenue-driven, malicious adware can track user behavior, redirect browsers to malicious sites, or install additional malware without consent.
Rootkits are one of the most difficult types of malware to detect and remove. These are designed to gain deep access to a system, allowing attackers to manipulate files, processes, and security tools while remaining hidden. Rootkits often disable antivirus programs and operate at the system’s kernel level, making them extremely persistent.
Each type of malware poses unique risks, requiring comprehensive security measures such as endpoint protection, firewalls, and behavior-based detection. By understanding these threats, users can take proactive steps to safeguard their devices and data from evolving cyberattacks.
Best Practices to Protect Against Malware and Viruses
Protecting against malware and viruses requires a proactive approach that combines cybersecurity tools, user awareness, and best practices to minimize vulnerabilities. Cybercriminals use a variety of attack methods, from phishing emails to exploit kits, making it essential to implement multiple layers of defense. By following best practices, individuals and organizations can significantly reduce the risk of infection and data breaches.
One of the most critical steps in malware and virus prevention is keeping software and operating systems updated. Cybercriminals exploit vulnerabilities in outdated software to deliver malware, so regular updates and patch management are essential. Enabling automatic updates ensures that security patches are applied as soon as they are available, reducing the risk of exploitation.
Using reputable antivirus and anti-malware software provides an additional layer of defense against malicious threats. Modern security solutions use signature-based detection, behavioral analysis, and machine learning to identify and remove malware before it can cause harm. While antivirus software is effective against known threats, advanced malware may require endpoint detection and response (EDR) solutions that offer real-time monitoring and threat containment.
Practicing safe browsing habits is another crucial measure in preventing infections. Avoid downloading software from untrusted sources, clicking on suspicious links, or opening email attachments from unknown senders. Phishing attacks remain one of the most common ways malware is distributed, so verifying email sources and using email security tools can help detect and block malicious attempts.
Implementing strong authentication methods enhances security by preventing unauthorized access. Multi-factor authentication (MFA) adds an extra layer of protection by requiring a second verification step, such as a one-time password (OTP) or biometric authentication. This makes it significantly harder for cybercriminals to compromise accounts, even if they obtain login credentials through phishing or data breaches.
Restricting user privileges and following the Principle of Least Privilege (PoLP) minimizes the impact of malware infections. Limiting administrative access ensures that users and applications only have the permissions necessary for their tasks, reducing the potential damage caused by malware or viruses. Privileged Access Management (PAM) tools can help enforce these restrictions by monitoring and controlling access to sensitive systems.
Regularly backing up data is an essential precaution against ransomware and other destructive malware. Automated, encrypted backups should be stored both on-premises and in the cloud to ensure data recovery in case of an attack. Businesses should also test their backup and disaster recovery plans to verify that critical systems can be restored quickly.
By combining cybersecurity tools, secure user practices, and regular monitoring, individuals and organizations can significantly reduce their risk exposure to malware and viruses. Staying informed about emerging threats and continuously updating security strategies ensures long-term protection in an evolving threat landscape.