What is a Windows Error Log?
A Windows error log is an entry recorded by the operating system whenever a system component, application, service, or security control experiences an error or warning.
These logs are automatically saved to the Windows Event Log, which tracks:
- System performance
- Software crashes
- Security events (e.g., logins, privilege changes)
- Application behavior
- Hardware failures
Each log entry contains a timestamp, source, severity level (Information, Warning, Error, or Critical),and a description of the event.
Why It Matters:
Windows error logs are essential for IT professionals. They help in:
- Diagnosing system crashes and slowdowns
- Investigating unauthorized access attempts
- Identifying patterns in recurring errors
- Providing forensic data during incident response
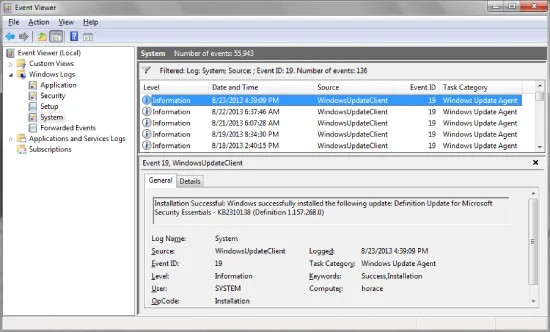
Where Are Windows Log Files Stored?
All Windows logs are stored in the Event Viewer, a built-in utility that organizes error data into categories. These logs are typically located at:
C:\Windows\System32\winevt\Logs\However, you don’t need to access them manually. Just open Event Viewer to view, filter, and analyze logs in real time.
How to Open Event Viewer to See Windows Error Logs
Follow these steps:
- Press Windows + R to open the Run dialog box.
- Type eventvwr and press Enter.
- The Event Viewer console opens.
From here, navigate through:
- Windows Logs → Includes Application, Security, Setup, System, and Forwarded Events
- Application and Services Logs → Specific logs for apps or services
Each log contains hundreds or thousands of entries—so use filters to find relevant errors or warnings.
How to Find Windows 10 Crash Logs
Crashes, blue screens (BSODs),and system hangs can be caused by faulty drivers, hardware issues, or software bugs. Here’s how to find Windows 10 crash logs:
- Open Event Viewer
- Navigate to Windows Logs > System
- Click Filter Current Log... on the right panel
- Select Error and Critical as event levels
- Look for events with source names like BugCheck, Kernel-Power, or EventLog
You can also use third-party tools like WhoCrashed or BlueScreenView to interpret crash dumps, but the Event Viewer gives you native access to the most detailed information.
Understanding the Windows Security Log
The Windows Security Log is one of the most critical sources of information for any IT admin or cybersecurity analyst.
It tracks:
- Logon/logoff activity
- Account creation, deletion, and privilege changes
- File and object access events
- Audit failures and policy changes
This log helps in:
- Detecting unauthorized access
- Tracing insider threats
- Complying with regulations (HIPAA, GDPR, etc.)
To view the Windows Security Log:
- Open Event Viewer
- Navigate to Windows Logs > Security
Use filters to isolate specific event IDs. For example:
- 4624: Successful logon
- 4625: Failed logon
- 4670: Permission changes
- 4688: Process creation
Types of Windows Log Files
Windows generates several types of logs. Understanding them helps you identify the right log for troubleshooting.
Application Logs
These logs are created by programs. They capture:
- App crashes
- Service failures
- Warnings generated by third-party software
System Logs
Generated by Windows OS components, system logs track:
- Driver failures
- Hardware issues
- System reboots
- Power outages
Security Logs
As discussed earlier, these logs track all security-related events. They are crucial for:
- Intrusion detection
- Privilege auditing
- Compliance monitoring
Setup Logs
These capture system setup activity, such as during OS installation or major upgrades.
Forwarded Events
Used in enterprise environments where logs from multiple devices are forwarded to a central server for analysis.
How to Use Windows Error Logs for Troubleshooting
- Identify Repeating Patterns
If a specific error appears frequently, it may point to a failing service, driver, or hardware component. - Correlate with User Complaints
When users report slowness or crashes, check timestamps and match them with error logs to identify root causes. - Trace Back from the Crash
Review events just before a crash to see if a specific driver or application caused the issue. - Use Event IDs for Deeper Research
Each log has an Event ID. Searching this ID in Microsoft’s documentation or tech forums can reveal fixes or known issues. - Export Logs for Support or Analysis
Right-click a log and choose Save All Events As to export logs for vendor support, legal documentation, or audit purposes.
Best Practices for Managing Windows Error Logs
- Clear old logs periodically to free up disk space
- Enable auditing for sensitive files and access attempts
- Set up alerts or email notifications for critical events
- Integrate with SIEM solutions (Security Information and Event Management)
- Use log forwarding to centralize visibility in enterprise environments
How Xcitium Enhances Windows Log Analysis
While Event Viewer is useful, it’s limited in automation, correlation, and threat detection. Xcitium elevates log analysis by integrating logs into a comprehensive security platform.
With Xcitium you get:
- Automated correlation between logs and real-time endpoint activity
- Threat intelligence to detect zero-day attacks and behavioral anomalies
- Centralized log management across endpoints and cloud environments
- Alert prioritization to focus on what matters most
- Incident response tools to take immediate action
Whether you're hunting for Windows 10 crash logs, reviewing the Windows Security Log, or managing thousands of log entries across devices—Xcitium gives you the tools to protect your business faster and more effectively.