What is a Golden Ticket Attack?
A Golden Ticket Attack is a type of cyberattack that targets Microsoft’s Kerberos authentication protocol within Active Directory environments. In a successful Golden Ticket Attack, an attacker forges a Ticket Granting Ticket (TGT) — essentially a master key that allows them to impersonate any user in the domain, including domain administrators, and gain unrestricted access to systems and data.
The attack gets its name from the famous “golden ticket” in Charlie and the Chocolate Factory, which gave the holder access to the entire chocolate factory. Similarly, a forged Kerberos golden ticket gives attackers the keys to the digital kingdom — often without detection.
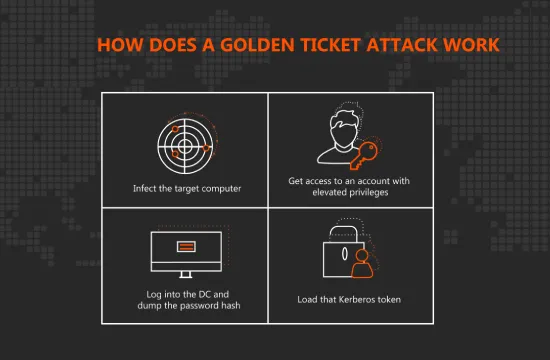
Golden Ticket Attacks typically begin with privilege escalation. The attacker must first obtain domain administrator rights or compromise a domain controller. Once inside, the attacker extracts the NTLM hash of the KRBTGT account, which is the Kerberos service account responsible for encrypting all authentication tickets in the domain. With this hash, the attacker can then use tools like Mimikatz to forge a custom TGT.
This forged TGT includes:
- Any username or user ID
- Any group memberships, including domain admin
- Any expiration date (including indefinite validity)
- Authentication data that appears legitimate to Kerberos
Because the ticket is cryptographically signed using the stolen KRBTGT hash, Kerberos believes it is valid, even though it was never issued by the domain controller.
The implications are severe. With a golden ticket, an attacker can:
- Access any system or resource within the domain
- Create or delete user accounts
- Steal sensitive data
- Maintain persistence for months or even years
What makes Golden Ticket Attacks particularly dangerous is how stealthy they are. Traditional security tools may not detect the attack because it doesn’t involve malware or obvious anomalies. The forged tickets look legitimate, and attackers can move laterally across the network without triggering alarms.
In short, a Golden Ticket Attack is not just a breach—it’s a complete domain compromise. That’s why it’s critical for organizations to understand how the attack works and implement safeguards like regular KRBTGT key rotation, strict privileged access controls, and proactive monitoring for unusual authentication patterns.
Why Golden Ticket Attacks Are So Dangerous?
Golden Ticket Attacks are considered one of the most dangerous threats to enterprise cybersecurity because they strike at the core of identity and access management within a Microsoft Active Directory environment. The primary reason these attacks are so dangerous is that they allow an attacker to generate their own authentication tickets—specifically, forged Kerberos Ticket Granting Tickets (TGTs)—which grant them unrestricted and often undetectable access to any resource on the network. These tickets are signed using the stolen hash of the KRBTGT account, which is the secret key used by the Kerberos Key Distribution Center (KDC). Once an attacker has that hash, they can impersonate any user, including domain administrators, and create tickets that are indistinguishable from legitimate ones.
The level of access granted through a Golden Ticket Attack is virtually unlimited. Attackers can move laterally across systems, access confidential files, modify security settings, exfiltrate sensitive data, and create backdoors for future access. Because the attack leverages valid Kerberos authentication flows, it bypasses many traditional security mechanisms like antivirus software, firewalls, or endpoint detection and response (EDR) systems. These systems often fail to detect malicious behavior because no malware is necessarily involved—everything appears to be functioning according to expected protocols.
Another dangerous aspect of Golden Ticket Attacks is persistence. An attacker can forge tickets with custom expiration dates, including ones that never expire. Unless the organization detects the breach and resets the KRBTGT password twice (a critical step in invalidating old tickets),the attacker can maintain long-term access. This makes Golden Ticket Attacks a favorite among advanced persistent threat (APT) groups that aim to remain inside a network undetected for long periods.
Detection is incredibly difficult. Since the forged tickets are cryptographically valid, security logs and monitoring systems may not flag them as suspicious. Attackers can blend into legitimate traffic, making forensic investigations complex and time-consuming. In many cases, organizations don’t realize they’ve been breached until significant damage has already been done.
Finally, Golden Ticket Attacks undermine trust in the organization’s entire identity infrastructure. Once Kerberos has been compromised at this level, every user and system within the domain must be considered suspect. Recovery from such an attack is costly and time-consuming, often requiring a complete re-architecture of the domain environment. This high impact, combined with the stealthy nature of the attack, is what makes Golden Ticket Attacks one of the most feared tactics in the modern threat landscape.
Real-World Examples of Golden Ticket Attacks
Real-world examples of Golden Ticket Attacks highlight just how devastating and stealthy this form of attack can be. While many organizations avoid publicly disclosing the technical details of breaches involving Golden Tickets, some high-profile incidents have brought attention to the severity of the threat. These examples provide insight into how attackers gain deep access, evade detection, and maintain long-term persistence within enterprise environments by exploiting Active Directory and the Kerberos authentication protocol.
One of the most cited real-world cases is the attack on the U.S. Office of Personnel Management (OPM) in 2015. While it involved multiple attack vectors, security researchers believe that after gaining initial access, the attackers used Golden Ticket techniques to move laterally within the network. By forging Kerberos tickets, they were able to impersonate privileged users, extract sensitive personnel records, and remain undetected for an extended period. The breach ultimately exposed the personal data of more than 21 million federal employees, highlighting the far-reaching consequences of such an attack.
Another notable example is the 2017 NotPetya cyberattack, which disrupted major organizations around the world, including Maersk, Merck, and FedEx. Although NotPetya was initially a destructive wiper disguised as ransomware, its rapid propagation was made possible by earlier reconnaissance and credential harvesting techniques. Some affected organizations reported signs of Golden Ticket-style attacks in the lead-up to the full-scale deployment of the malware, suggesting attackers had established deep access and persistence using forged tickets before launching the destructive phase.
Advanced Persistent Threat (APT) groups such as APT29 (Cozy Bear) and APT28 (Fancy Bear),both associated with Russian state-sponsored activity, have also been linked to Golden Ticket techniques. These groups often conduct long-term cyber espionage campaigns, and forging Kerberos tickets gives them the ability to quietly maintain access to critical systems for extended periods. For example, during campaigns against U.S. government agencies and defense contractors, these threat actors reportedly leveraged Golden Ticket attacks to avoid detection while exfiltrating sensitive information.
Large private sector organizations have also fallen victim. In one case disclosed by Mandiant, an unnamed Fortune 500 company experienced a Golden Ticket Attack after a phishing campaign led to domain admin access. The attackers used Mimikatz to extract the KRBTGT hash, forged golden tickets, and maintained access for over six months, bypassing multiple layers of security controls.
These real-world cases demonstrate that Golden Ticket Attacks are not hypothetical—they are actively used by some of the world’s most sophisticated adversaries. They underscore the need for organizations to implement proactive security measures, monitor authentication behavior closely, and regularly rotate the KRBTGT key to reduce the risk of undetected long-term compromise.
Golden Ticket Attack vs Other Kerberos Attacks
When comparing Golden Ticket Attacks to other Kerberos-based attacks, it becomes clear that while they share some technical foundations, Golden Tickets are uniquely powerful in terms of access and persistence. Kerberos, as the default authentication protocol in Microsoft Active Directory environments, is a high-value target for attackers. Understanding the differences between various Kerberos attacks is essential for building strong defenses.
A Golden Ticket Attack involves forging a valid Kerberos Ticket Granting Ticket (TGT) using the NTLM hash of the KRBTGT account. This hash is extracted from the domain controller after the attacker has obtained domain administrator privileges. Once this hash is in hand, the attacker can generate TGTs that allow them to impersonate any user in the domain—even high-level admins—without needing to authenticate through the standard login process. These tickets can also be set with custom expiration dates, enabling long-term access. Because the forged ticket is cryptographically valid, it often goes undetected by traditional security monitoring tools.
In contrast, a Silver Ticket Attack is another form of Kerberos abuse, but it targets Service Tickets (TGS) rather than TGTs. Silver Ticket Attacks involve forging service-specific Kerberos tickets by compromising the NTLM hash of a service account, such as one used by SQL Server or SharePoint. While this gives attackers access to a particular service, it does not provide domain-wide access. Silver Tickets are easier to detect than Golden Tickets because they interact directly with services and don’t involve the Key Distribution Center (KDC),which logs ticket activity. However, Silver Ticket Attacks still pose a serious threat, particularly in lateral movement scenarios.
Pass-the-Ticket (PtT) is another Kerberos-related attack technique. Rather than forging tickets, attackers steal legitimate Kerberos tickets from a user’s session and inject them into their own session to access systems as that user. This technique doesn't require knowledge of encryption keys but still enables privilege escalation and lateral movement. Pass-the-Ticket attacks rely on gaining access to a system where the target user has an active session, typically through credential dumping or remote access tools.
Pass-the-Hash (PtH),while not strictly a Kerberos attack, is often used in conjunction with these methods. It involves using NTLM password hashes to authenticate without cracking passwords. In hybrid attacks, attackers may use Pass-the-Hash to escalate privileges and then pivot to Kerberos-based attacks like Golden Ticket or Silver Ticket.
Among these, Golden Ticket Attacks are considered the most severe because they provide complete control over the domain with the ability to create undetectable tickets for any user or service. While other attacks offer privilege escalation or service-level access, only Golden Ticket Attacks undermine the trust model of the entire Kerberos authentication system. This makes them not only dangerous but also one of the hardest threats to detect and remediate once active in a network.
How to Detect a Golden Ticket Attack
Detecting a Golden Ticket Attack is notoriously difficult due to the way forged Kerberos tickets closely mimic legitimate ones. Unlike malware-based attacks that can leave digital fingerprints or behavioral anomalies, Golden Ticket Attacks operate within the boundaries of the Kerberos authentication protocol. Because the forged tickets are cryptographically valid—signed using the stolen KRBTGT account hash—most traditional security tools and logs do not flag them as suspicious. However, there are several indicators and detection strategies that organizations can implement to improve their chances of identifying this type of advanced persistent threat.
One of the most effective ways to detect a Golden Ticket Attack is by monitoring for unusual Kerberos ticket activity. Golden Tickets often have abnormal characteristics, such as extended or infinite expiration dates, forged usernames, or unusual group memberships like domain admin rights. Monitoring for Kerberos tickets with unusually long lifespans or inconsistencies in the ticket metadata can raise red flags. These anomalies can be identified using tools like Security Information and Event Management (SIEM) platforms, which can correlate and analyze authentication patterns across the network.
Event log analysis is also essential. In particular, Windows Security Event ID 4769 (A Kerberos service ticket was requested) and Event ID 4768 (A Kerberos authentication ticket was requested) can provide useful data points. Repeated authentication requests for sensitive services from unexpected accounts or workstations should be investigated. Additionally, monitoring for Event ID 4624 (successful logon) with logon type 3 (network) from suspicious accounts or machines can help detect lateral movement using forged tickets.
Another detection method involves monitoring domain controllers for abnormal activity. Since Golden Ticket Attacks bypass the typical Kerberos ticket issuance process, there may be a lack of corresponding TGT requests for certain user sessions. If a user is accessing multiple resources across the network without any record of an initial ticket request from the domain controller, this could indicate forged TGT usage.
Security teams should also watch for “impossible travel” behavior or access from systems outside the normal operating pattern of a user account. If a user who typically logs in from a specific device suddenly appears to be accessing sensitive systems from multiple endpoints or at odd hours, it may be the result of a forged Golden Ticket being used by an attacker.
Because detection is challenging, many organizations rely on proactive defenses such as tiered admin models, restricted use of domain admin accounts, and frequent KRBTGT account password resets. These measures reduce the window of opportunity for attackers and make it easier to correlate suspicious behavior if a Golden Ticket is in use.
Ultimately, while no single indicator confirms a Golden Ticket Attack, combining behavioral analysis, ticket anomaly detection, and strong security hygiene can significantly improve an organization’s ability to detect and respond to these stealthy and damaging intrusions.
How to Prevent Golden Ticket Attacks in Active Directory
Preventing Golden Ticket Attacks in an Active Directory environment requires a proactive and layered security strategy. Because Golden Ticket Attacks exploit the Kerberos authentication system by forging Ticket Granting Tickets (TGTs),organizations must take steps to protect the core components of that system—particularly the KRBTGT account, domain controllers, and privileged credentials. While no single defense can eliminate the risk, a combination of best practices can significantly reduce the chances of a successful attack and limit the damage if one occurs.
The most important step in prevention is protecting the KRBTGT account, which holds the encryption keys used to sign Kerberos tickets. If an attacker compromises this account’s NTLM hash, they can forge golden tickets that appear legitimate to the domain controller. To reduce this risk, organizations should regularly rotate the KRBTGT password. Microsoft recommends resetting the password twice in succession to invalidate existing tickets and keys. This should be done periodically, especially after a suspected breach, to limit how long a compromised hash can be used.
Another key prevention strategy is limiting domain administrator privileges. Golden Ticket Attacks require domain admin or equivalent rights to access and dump the KRBTGT hash. Implementing a tiered administrative model helps minimize the exposure of these powerful accounts. Admin accounts should be used only when absolutely necessary and from secure, hardened machines. Service accounts should also be limited in scope and monitored closely, as they are often targets for attackers seeking to escalate privileges.
Securing domain controllers is also crucial. These systems should be isolated from general network traffic and tightly monitored. Implementing network segmentation, firewall restrictions, and application whitelisting can reduce the chances of an attacker reaching or executing malicious tools on a domain controller. Multi-factor authentication (MFA) should be enforced for all privileged accounts to make initial compromise more difficult.
Regular monitoring and auditing are critical for identifying suspicious activity that may precede a Golden Ticket Attack. This includes unusual login patterns, anomalous Kerberos ticket usage, and failed attempts to access sensitive systems. Deploying tools such as SIEM, EDR, or advanced identity threat detection solutions can help detect precursors to ticket forgery attempts.
Finally, educating administrators and security personnel about the mechanics of Golden Ticket Attacks and maintaining a strong incident response plan ensures the team can act quickly if suspicious activity is detected. While these attacks are difficult to detect and defend against, a well-maintained, least-privilege Active Directory environment with proactive monitoring can significantly reduce the attack surface and impact of a potential compromise.