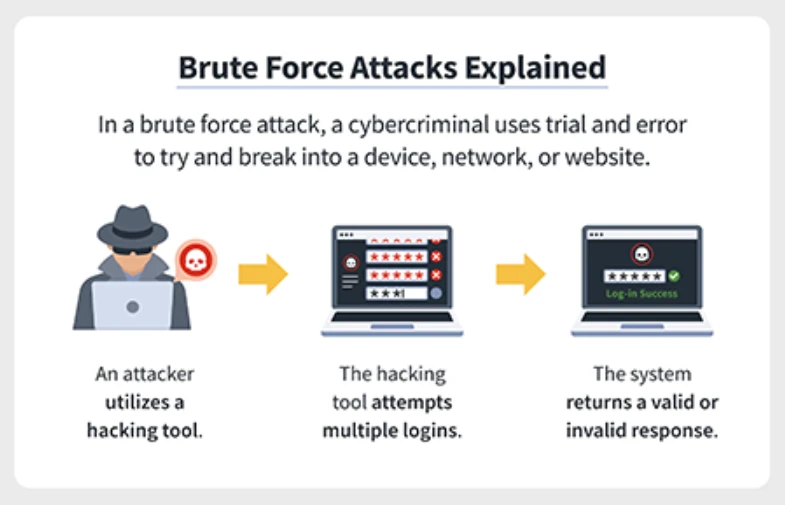
What are Brute Force Attacks?
A brute force attack is a straightforward yet powerful method used by cybercriminals to break into systems, accounts, or encrypted data. At its core, it’s a trial-and-error approach where an attacker systematically attempts every possible combination of passwords, PINs, or encryption keys until the correct one is found. Think of it like trying every key on a massive keyring to unlock a door—eventually, one will fit. While this might sound time-consuming, modern computing power and automated tools make brute force attacks a real and persistent threat to cybersecurity.
The concept is simple: attackers rely on the likelihood that many people use weak, predictable passwords—like "123456" or "password"—or fail to secure their systems adequately. With the help of specialized software, such as password-cracking tools, hackers can test thousands, even millions, of combinations per second. These tools often run on powerful hardware or cloud-based systems, amplifying their speed and efficiency. In some cases, attackers target specific accounts, like an admin login, while in others, they cast a wide net, hitting multiple users across a platform.
Brute force attacks don’t discriminate—they can target anything from your personal email to a corporate database. Websites, online services, and even IoT devices like smart cameras are all fair game. The goal is unauthorized access, whether to steal sensitive data, install malware, or hijack accounts for further exploitation. What makes these attacks particularly insidious is their persistence; they don’t require sophisticated hacking skills, just patience and the right resources.
There are variations of brute force attacks that refine the approach. A "simple" brute force attack tries every possible character combination (e.g., "aaa," "aab," "aac," and so on),which works well against short or basic passwords. More advanced versions, like dictionary attacks, use precompiled lists of common passwords or phrases, speeding up the process by guessing likely candidates first. Hybrid attacks combine these methods, mixing random characters with dictionary words for greater efficiency.
Why do brute force attacks succeed? Often, it’s human error. Weak passwords, reused credentials, and a lack of additional security layers—like two-factor authentication (2FA)—leave the door wide open. While they may not always be the most elegant cyberthreat, brute force attacks remain effective because they exploit these vulnerabilities relentlessly. Understanding their mechanics is crucial for anyone looking to bolster their defenses, whether you’re safeguarding personal accounts or protecting a business from data breaches.
How to Detect a Brute Force Attack
Detecting a brute force attack early is critical to minimizing damage and securing your systems. Since these attacks rely on repeatedly guessing passwords or credentials, they leave telltale signs that vigilant users and administrators can spot. Unlike stealthier cyberattacks, brute force attempts often generate noticeable patterns of activity—think of it as a burglar loudly rattling every window to find one that’s unlocked. By recognizing these red flags, you can take swift action to block attackers and protect sensitive data.
One of the most obvious signs is an unusual spike in failed login attempts. If you or your system logs show multiple unsuccessful logins—especially in quick succession—it’s a strong indicator that someone is hammering away at your defenses. For individual users, this might look like repeated "incorrect password" notifications on your email or banking app. For businesses, server logs might reveal hundreds of failed attempts targeting a single account or spread across multiple users. Monitoring tools like intrusion detection systems (IDS) can flag this behavior automatically, alerting you to potential threats.
Another clue is the timing and source of login attempts. Brute force attacks often originate from unfamiliar IP addresses, sometimes overseas, or from known malicious networks. If your account dashboard shows login tries from a country you’ve never visited, or at odd hours when you’re typically offline, it’s worth investigating. Attackers may also use botnets—networks of hijacked devices—to distribute their attempts, so you might see a flurry of activity from multiple, unrelated IPs. Tools like geo-blocking or IP whitelisting can help filter out suspicious traffic before it becomes a problem.
System performance can also tip you off. Since brute force attacks bombard servers with requests, you might notice slowdowns, crashes, or unusual resource usage. For website owners, this could mean slower load times or a spike in bandwidth consumption. Security logs are your best friend here—check for patterns like rapid-fire requests to login pages or API endpoints. Many platforms, like WordPress or cloud services, offer built-in analytics to track this activity, making it easier to spot anomalies.
Finally, user reports can be a frontline defense. If employees or customers complain about account lockouts or strange login prompts, it could signal a brute force attempt in progress. Combining these detection methods—monitoring logs, watching for odd patterns, and leveraging security tools—gives you a solid shot at catching attackers before they break through.
Preventing Brute Force Attacks
Preventing brute force attacks is all about building strong defenses that make it too hard, too slow, or too costly for attackers to succeed. Since these attacks thrive on exploiting weak passwords and unsecured systems, the key is to eliminate those vulnerabilities and add layers of protection. By taking proactive steps, you can stop cybercriminals in their tracks—whether they’re targeting your personal accounts or an entire business network. Here’s how to fortify your cybersecurity and keep brute force attackers at bay.
The first line of defense is a strong, unique password. Weak passwords like "password123" are a hacker’s dream, cracked in seconds by brute force tools. Instead, use long, complex combinations—at least 12 characters—mixing letters, numbers, and symbols. Password managers can help generate and store these securely, so you don’t have to memorize them. Avoid reusing passwords across accounts; if one gets compromised, attackers often try it elsewhere. Encouraging or enforcing strong password policies is especially critical for businesses managing multiple users.
Two-factor authentication (2FA) is a game-changer. Even if an attacker guesses your password, 2FA requires a second step—like a code sent to your phone or an authenticator app—making brute force attempts nearly useless. It’s simple to set up on most platforms, from email to banking, and adds a barrier that automated tools can’t easily bypass. For organizations, mandating 2FA across all accounts can drastically reduce the risk of breaches.
Rate limiting and account lockouts are also powerful tools. Rate limiting caps how many login attempts can happen in a set time, slowing attackers down. Account lockouts temporarily disable an account after a certain number of failed tries—say, five or ten—stopping brute force scripts cold. Many websites and servers, like WordPress or cloud platforms, offer these features built in. Just be sure to balance security with usability so legitimate users aren’t frustrated.
Finally, advanced measures like CAPTCHAs or web application firewalls (WAFs) should be considered. CAPTCHAs—those "prove you’re not a robot" tests—block automated scripts from flooding login pages. WAFs filter out malicious traffic before it reaches your system, often identifying and blocking brute force patterns. For businesses, regularly updating software and monitoring logs for suspicious activity can catch weak spots early. By combining these strategies—strong passwords, 2FA, lockouts, and tech defenses—you create a fortress that brute force attackers can’t crack easily, keeping your data safe.