What is the Cyberattack Kill Chain (CKC)?
The Cyberattack Kill Chain (CKC) is a cybersecurity framework developed by Lockheed Martin to describe the sequential stages of a cyberattack. It provides security professionals with a structured approach to identifying and mitigating cyber threats by breaking down an attack into distinct phases. The concept is based on military strategies where adversaries follow a predictable process to achieve their objectives, allowing defenders to anticipate and disrupt their actions before they succeed.
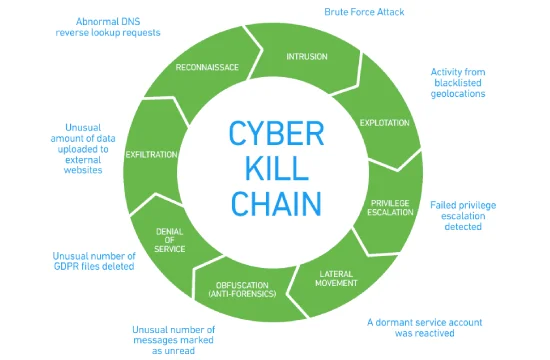
The Cyberattack Kill Chain consists of seven primary stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. The first stage, reconnaissance, involves cybercriminals gathering information about their target, such as identifying vulnerabilities, mapping network infrastructure, and collecting employee details. This phase is crucial for attackers as it helps them determine the most effective way to breach a system. The second stage, weaponization, is where attackers create malicious payloads, such as malware or exploits, designed to take advantage of the weaknesses identified during reconnaissance.
In the delivery phase, attackers deploy their weaponized payloads through various means, including phishing emails, malicious attachments, drive-by downloads, or compromised websites. Once the payload reaches the target, the exploitation phase begins, where the attacker takes advantage of a security vulnerability to execute malicious code and gain unauthorized access to the system. The installation stage follows, where the attacker establishes persistence by installing malware, backdoors, or rootkits that allow continuous access even if the initial entry point is closed.
After installation, the attacker sets up a command and control (C2) channel, enabling remote control over the compromised system. This phase allows attackers to execute commands, move laterally across the network, and exfiltrate sensitive data. Finally, the last stage, actions on objectives, is where the attacker achieves their ultimate goal, such as data theft, financial fraud, espionage, or system destruction. At this point, the attacker may encrypt files, delete logs, or deploy ransomware to maximize damage.
Understanding the Cyberattack Kill Chain helps organizations implement proactive defense strategies. By identifying attacks in the early stages, security teams can disrupt or mitigate threats before they escalate. Techniques such as real-time monitoring, threat intelligence, Zero Trust security models, and advanced endpoint protection solutions can help break the chain and prevent cyber incidents. Modern cybersecurity frameworks, such as the MITRE ATT&CK framework, have expanded upon CKC, providing more granular details on attack tactics and techniques. However, CKC remains a foundational concept for cybersecurity professionals in structuring their defense strategies against evolving threats.
The Evolution of CKC in Modern Cybersecurity
The Cyberattack Kill Chain (CKC) was originally developed by Lockheed Martin as a way to map out the lifecycle of a cyberattack. While it remains a valuable framework, cybersecurity threats have evolved significantly since its inception, requiring organizations to adapt their defensive strategies accordingly. The traditional CKC model was designed primarily for perimeter-based security approaches, focusing on stopping attacks at the network entry point. However, with the rise of sophisticated cyber threats, including advanced persistent threats (APTs),ransomware, and insider threats, modern cybersecurity has had to refine and expand upon the CKC model.
One of the key limitations of the original CKC framework is its linear approach. It assumes that cyberattacks follow a predictable, sequential process, but modern adversaries often bypass or combine multiple stages to avoid detection. Cybercriminals have adopted more advanced techniques, such as fileless malware, supply chain attacks, and living-off-the-land (LotL) tactics, which exploit legitimate system tools rather than relying on traditional malware payloads. This has made detection and mitigation more complex, as attackers continuously refine their methods to evade traditional security measures.
To address these evolving threats, cybersecurity frameworks have expanded beyond CKC to include models such as the MITRE ATT&CK framework. Unlike CKC, which focuses on high-level attack stages, MITRE ATT&CK provides a detailed matrix of tactics and techniques used by threat actors, offering a more granular approach to threat detection and response. Organizations now leverage a combination of CKC and MITRE ATT&CK to gain deeper insights into attack methodologies and develop more robust security postures.
Another major advancement in modern cybersecurity is the adoption of Zero Trust architecture, which challenges the traditional perimeter-based security model. Zero Trust assumes that threats can originate from both external and internal sources, enforcing strict identity verification and continuous monitoring of all users, devices, and network activity. This approach directly addresses gaps in the CKC model by reducing the attack surface and limiting an adversary’s ability to move laterally within an environment.
Cybersecurity teams have also integrated artificial intelligence (AI) and machine learning (ML) to detect and respond to threats more efficiently. AI-driven security tools analyze vast amounts of data to identify patterns, anomalies, and potential attack indicators in real time. By leveraging behavioral analytics, organizations can detect deviations from normal activity and prevent attacks before they escalate.
While the CKC remains a foundational concept in cybersecurity, modern organizations must adapt it to today’s dynamic threat landscape. By incorporating advanced threat intelligence, behavioral analytics, and Zero Trust principles, businesses can proactively defend against sophisticated attacks that go beyond the traditional kill chain model.
Cyberattack Kill Chain vs. MITRE ATT&CK Framework
The Cyberattack Kill Chain (CKC) and the MITRE ATT&CK Framework are two widely used models in cybersecurity that help organizations understand and defend against cyber threats. While both frameworks focus on identifying and mitigating cyberattacks, they differ in their structure, scope, and application. The CKC provides a high-level overview of the sequential stages of a cyberattack, whereas MITRE ATT&CK offers a more granular, real-world representation of adversary tactics and techniques.
The Cyberattack Kill Chain, developed by Lockheed Martin, outlines seven key stages of a cyberattack: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. This model helps security teams identify potential breaches at different points in the attack lifecycle and implement preventative measures to break the chain before an attack is fully executed. CKC is particularly useful for designing defensive strategies that focus on early-stage threat detection and prevention.
However, one of CKC’s main limitations is its linear approach. It assumes that attacks follow a predictable sequence, which may not always be the case in modern cyber threats. Many adversaries now bypass certain stages, use fileless malware, or employ living-off-the-land (LotL) techniques that do not require traditional payloads. These advanced attack methods often evade signature-based detection, rendering CKC less effective as a sole security strategy.
The MITRE ATT&CK Framework, on the other hand, takes a more detailed and flexible approach by categorizing tactics, techniques, and procedures (TTPs) used by real-world threat actors. Unlike CKC, which follows a fixed progression, MITRE ATT&CK presents a matrix of attack techniques mapped to specific adversary behaviors. These techniques are constantly updated based on real-world threat intelligence, making ATT&CK a dynamic and evolving resource for cybersecurity teams.
One of the biggest advantages of MITRE ATT&CK is its real-world applicability. Security teams can use it to simulate attacks, conduct threat hunting, and improve incident response strategies. It provides insight into how different attack techniques work, what threat actors are using them, and how organizations can detect and mitigate these tactics at different points in the attack lifecycle.
While CKC remains useful for understanding the general structure of cyberattacks, MITRE ATT&CK is more comprehensive and adaptable to today’s rapidly evolving threat landscape. Many organizations now integrate both frameworks, using CKC for high-level attack modeling and ATT&CK for detailed threat detection and response. By leveraging both, cybersecurity teams can create a proactive defense strategy that addresses traditional and emerging cyber threats.