Zero Trust Cybersecurity from Endpoints to Cloud Workloads
Our patented zero trust auto-containment technology protects endpoints, networks, and cloud workloads from zero-day threats by isolating unknowns at run-time until they are analyzed and verdicted, good or bad.
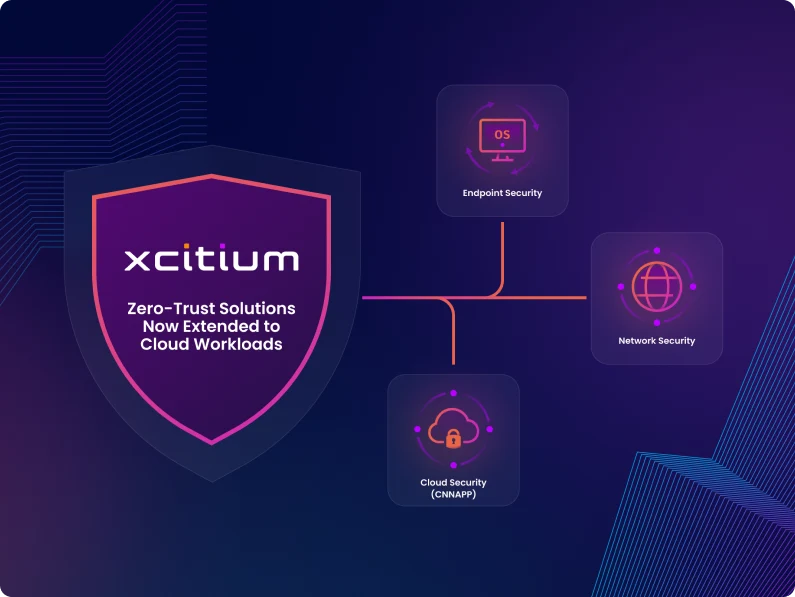
Single Pane-of-Glass Platform
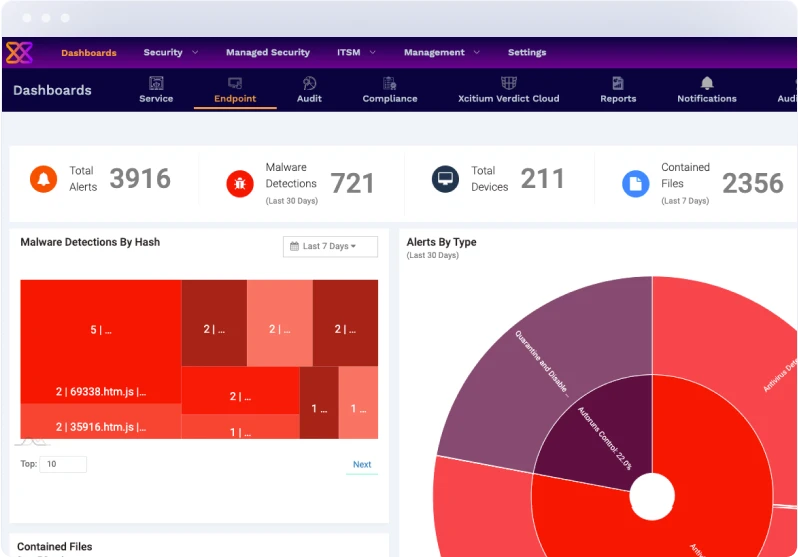
Xcitium’s Zero Trust Auto Containment protects endpoints, networks, and cloud workloads from zero-day threats and allows you to run your business without fear of malware or ransomware.
How it Works

Pre-Execution
- NextGen EDR
- Host Intrusion Prevention
- Host Firewall
- VirusScope Static Analysis
- Application Control
At Execution
Unknowns are allowed to execute in Virtual Resources, where they can’t do any damage.

Post-Execution
- Unkown Good Whitelisted
- Unknown Bad blacklisted
- Combination of Automated and Human Analysis
Detection ≠ Protection

- Security Models only recognize and prevent known malware, leaving you vulnerable to unknown threats
- There is always a lag when new malware is introduced, and a solution can be created
- The zero-day threat lag means you are unprotected during that window

- Unknowns Contained , Classified good and bad in Virtual mode.
- Allows executables to run in virtualized containers where they can’t do any damage
- Applies a verdicting process with minimal impact in performance and user experience
Testimonials
Real Customer Results
Organizations around the world rely on Xcitium’s innovative solutions to help bring
zero-trust posture from their endpoints to their cloud, under a single pane of glass.
Review weekly proof of our zero trust containment protection. New malware and ransomware always start their lives as Unknowns. That’s why detection-based products miss these detection and allow breaches to occur. Review weekly proof of our zero trust containment here.
of active devices with potential malicious activity (in-containment)
of active devices on known good state (no unknowns)
of active devices with infection or breach
of the unknown that turn out to be malware
Why Choose Xcitium?
Xcitium exists to ensure that people can embrace technology fully, without the shadow of insecurity hanging over them. We’re here to give users the freedom to explore, create, and connect without fear. Whether it’s preventing unknown files from compromising systems or offering innovative approaches to endpoint protection solution, Xcitium’s technology is designed to foster confidence. We believe that by keeping the digital ecosystem secure, we’re directly contributing to human evolution—by enabling people to take full advantage of the tools that define our era.

When you visit any website, it may store or retrieve information on your browser, mostly in the form of cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not usually directly identify you, but it can give you a more personalized web experience. Because we respect your right to privacy, you can choose not to allow some types of cookies. Click on the different category headings to find out more and change our default settings. However, blocking some types of cookies may impact your experience of the site and the services we are able to offer.











